How to 100% pass 70-417 exam? GreatExam provides the guaranteed 70-417 exam preparation material to boost up your confidence in 70-417 exam. Successful candidates have provided their reviews about our 70-417 dumps. Now GreatExam supplying the new version of 70-417 VCE and PDF dumps. We ensure our 70-417 exam questions are the most complete and authoritative compared with others’, which will ensure your 70-417 exam pass.
QUESTION 521
A computer does not support PXE, what kind of image do you need to create?
A. boot
B. install
C. discovery
D. capture
Answer: C
QUESTION 522
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012. One of the domain controllers is named DC1.
The DNS zone for the contoso.com zone is Active Directory-integrated and has the default settings. A server named Server1 is a DNS server that runs a UNIX-based operating system.
You plan to use Server1 as a secondary DNS server for the contoso.com zone.
You need to ensure that Server1 can host a secondary copy of the contoso.com zone.
What should you do?
A. From Windows PowerShell, run the Set-DnsServerForwarder cmdlet and specify the contoso.com zone as a target.
B. From Windows PowerShell, run the Set-DnsServerSetting cmdlet and specify DC1 as a target.
C. From Windows PowerShell, run the Set-DnsServerPrimaryZone cmdlet and specify the contoso.com zone as a target.
D. From DNS Manager, modify the Advanced settings of DC1.
Answer: C
Explanation:
By default, allowed no zone transfer to other DNS servers for Active Directory-integrated zone. The replication of zone data is in Active Directory-integrated zones solely within the framework of the Active Directory replication.
To enable Server1 obtaining the zone data, the settings of the zone transfer for certbase.de need to be changed. This can either be on the characteristics of the zone in DNS Manager or by using the PowerShell cmdlet Set-DnsServerPrimaryZone done.
QUESTION 523
You are the administrator of an Active Directory Domain Services (AD DS) domain named contoso.com. The domain has a Microsoft Windows Server 2012 R2 server named Contoso-SR05 that hosts the File and Storage Services server role.
Contoso-SR05 hosts a shared folder named userData.
You want to receive an email alert when a multimedia file is saved to the userData folder.
Which tool should you use?
A. You should use File Management Tasks in File Server Resource Manager.
B. You should use File Screen Management in File Server Resource Manager.
C. You should use Quota Management in File Server Resource Manager.
D. You should use File Management Tasks in File Server Resource Manager.
E. You should use Storage Reports in File Server Resource Manager.
Answer: B
QUESTION 524
You have two servers, Server 1 and server 2.
You create a custom data collector set DCS1 on Server 1.
You need to export DCS1 from Server 1 to Server2.
What should you do?
A. Right click on DCS1 and click on Export list
B. Right click on DCS1 and click on Save template
C. Right click on DCS1 and click on Data Manager
D. Right click on DCS1 and click on Export manager
Answer: B
Explanation:
The function Save Template … lets you export the definition of a data collector set in an XML file. Subsequently, the Data Collector Set can be imported on Server2.
QUESTION 525
You administrate an Active Directory domain named EnsurePass.com.
The domain has a Microsoft Windows Server 2012 R2 server named EP-SR01 that hosts the File Server Resource Manager role service.
You are configuring quota threshold and want to receive an email alert when 80% of the quota has been reached.
Where would you enable the email alert?
A. You should consider creating a Data Collector Set (DCS).
B. You should use Windows Resource Monitor.
C. You should use the File Server Resource Manager.
D. You should use Disk Quota Tools.
E. You should use Performance Logs and Alerts.
Answer: C
Explanation:
To make use of email alerts, you need to configure the SMTP Server address details in the File Server Resource Manager options.
QUESTION 526
Note: This Question is part of series of question that use the same or similar answer choices.
An answer choice may be correct for more than one question in the series. Each question is independent of the other questions in the series. Information and detailed provided in a question apply only to that question. You network contains one Active Directory domain named contoso.com. The forest functional level is Windows Server 2012. All servers run Windows Server 2012 R2. All client computer run Windows 8.1.
The domain contains 10 domain controllers and a read-only domain controller (RODC) named RODC01. All domain controllers and RODCs are hosted on a Hyper-V host that runs Windows Server 2012 R2.
You need to identify which domain controllers are authorized to be cloned using virtual domain controller cloning.
Which cmdlet should you use?
A. Get-ADGroupMember
B. Get-ADDomainControllerPasswordReplicationPolicy
C. Get-ADDomainControllerPasswordReplicationPolicyUsage
D. Get-ADDomain
E. Get-ADOptionalFeature
F. Get-ADAccountAuthorizationGroup
G. Get-ADAuthenticationPolicySlio
H. Get-ADAuthenticationPolicy
Answer: A
QUESTION 527
Note: This Question is part of series of question that use the same or similar answer choices.
An answer choice may be correct for more than one question in the series. Each question is independent of the other questions in the series. Information and detailed provided in a question apply only to that question. You network contains one Active Directory domain named contoso.com. The forest functional level is Windows Server 2012.
All servers run Windows Server 2012 R2. All client computer run Windows 8.1.
The domain contains 10 domain controllers and a read-only domain controller (RODC) named RODC01.
All domain controllers and RODCs are hosted on a Hyper-V host that runs Windows Server 2012 R2. You need to identify which security principals are authorized to have their password cached on RODC1? Which cmdlet should you use?
A. Get-ADGroupMember
B. Get-ADDomainControllerPasswordReplicationPolicy
C. Get-ADDomainControllerPasswordReplicationPolicyUsage
D. Get-ADDomain
E. Get-ADOptionalFeature
F. Get-ADAccountAuthorizationGroup
G. Get-ADAuthenticationPolicySlio
H. Get-ADAuthenticationPolicy
Answer: B
QUESTION 528
Note: This Question is part of series of question that use the same or similar answer choices.
An answer choice may be correct for more than one question in the series. Each question is independent of the other questions in the series. Information and detailed provided in a question apply only to that question. You network contains one Active Directory domain named contoso.com. The forest functional level is Windows Server 2012.
All servers run Windows Server 2012 R2. All client computer run Windows 8.1.
The domain contains 10 domain controllers and a read-only domain controller (RODC) named RODC01. All domain controllers and RODCs are hosted on a Hyper-V host that runs Windows Server 2012 R2. Determine what domain controller needs to be online to promote a RODC.
Which cmdlet should you use?
A. Get-ADGroupMember
B. Get-ADDomainControllerPasswordReplicationPolicy
C. Get-ADDomainControllerPasswordReplicationPolicyUsage
D. Get-ADDomain
E. Get-ADOptionalFeature
F. Get-ADAccountAuthorizationGroup
G. Get-ADAuthenticationPolicySlio
H. Get-ADAuthenticationPolicy
Answer: D
QUESTION 529
Note: This Question is part of series of question that use the same or similar answer choices.
An answer choice may be correct for more than one question in the series. Each question is independent of the other questions in the series. Information and detailed provided in a question apply only to that question. You network contains one Active Directory domain named contoso.com. The forest functional level is Windows Server 2012.
All servers run Windows Server 2012 R2. All client computer run Windows 8.1. The domain contains 10 domain controllers and a read-only domain controller (RODC) named RODC01.
All domain controllers and RODCs are hosted on a Hyper-V host that runs Windows Server 2012 R2. What accounts are allowed to replicate their password with the RODC? Which cmdlet should you use?
A. Get-ADGroupMember
B. Get-ADDomainControllerPasswordReplicationPolicy
C. Get-ADDomainControllerPasswordReplicationPolicyUsage
D. Get-ADDomain
E. Get-ADOptionalFeature
F. Get-ADAccountAuthorizationGroup
G. Get-ADAuthenticationPolicySlio
H. Get-ADAuthenticationPolicy
Answer: B
QUESTION 530
Note: This Question is part of series of question that use the same or similar answer choices.
An answer choice may be correct for more than one question in the series. Each question is independent of the other questions in the series. Information and detailed provided in a question apply only to that question. You network contains one Active Directory domain named contoso.com. The forest functional level is Windows Server 2012. All servers run Windows Server 2012 R2. All client computer run Windows 8.1.
The domain contains 10 domain controllers and a read-only domain controller (RODC) named RODC01. All domain controllers and RODCs are hosted on a Hyper-V host that runs Windows Server 2012 R2. You need to identify whose passwords can be stored, view stored passwords.
Which cmdlet should you use?
A. Get-ADGroupMember
B. Get-ADDomainControllerPasswordReplicationPolicy
C. Get-ADDomainControllerPasswordReplicationPolicyUsage
D. Get-ADDomain
E. Get-ADOptionalFeature
F. Get-ADAccountAuthorizationGroup
G. Get-ADAuthenticationPolicySlio
H. Get-ADAuthenticationPolicy
Answer: C
QUESTION 531
You have a DNS server that runs Windows Server 2012 R2.
The server hosts the zone for contoso.com and is accessible from the internet.
You need to create a DNS record for the Sender Policy Framework (SPF) to list that are authorized ti send email for contoso.com
Which type of record should you create?
A. Name Server (NS)
B. Mail.exchanger (MX)
C. Resource record signature (RRSIG)
D. Text (TXT)
Answer: D
Explanation:
http://mediatemple.net/community/products/dv/204404314/how-can-i-create-an-spf-record-for-my-domain
http://en.wikipedia.org/wiki/Sender_Policy_Framework
QUESTION 532
You have three Windows Server Update Services (WSUS) Servers named Server01 Server02 and Server03.
Server01 synchronizes form Microsoft Update.
You need to ensure that only Server02 and Server03 can Synchronize updates from Server01.
What should you do?
A. Modify %ProgramFiles%\Update Services\WebServices\Serversyncgwevservice\SimpleAuth.asmx.
B. From the Update Services console, modify the Update Source and Proxy Server options.
C. From the Update Services console, modify the Automatic Approvals Options.
D. Modify %ProgramFiles%\Update Services\WebServices\Serversyncgwevservice\Web.config.
Answer: D
Explanation:
“The question is asking how to harden WSUS, i.e. limit the servers that can get updates from Server01 to only Server02 and Server03. This is done by modifying the web.config. ” https://technet.microsoft.com/en-us/library/Cc708550(v=WS.10).aspx
QUESTION 533
Your corporate network includes an Active Directory Domain Services (AD DS) domain certbase.de named.
The domain contains a Windows Server 2012 R2 computer named Server3. Server3 performs the role Windows Deployment Services.
They have a virtual Windows Server 2012 R2 creates computer named VM1.
On VM1 several industry-specific applications are installed.
To use the Windows Deployment Services to create an image of VM1.
What image type you will add Server3?
A. Capture
B. Install
C. Discovery
D. Boot
Answer: A
Explanation:
The main image types used in Windows Deployment Services are installation and boot images.
Install images
Install images are the operating system images that you deploy to the client computer. You can use the default install image (install.wim) located on the DVD of Windows Vista or Windows Server 2008 in the \ Sources directory.
You can also create custom install images from reference computers and deploy them to client computers. First, you boot a computer (which has been prepared with Sysprep) into a capture image. Then the capture image an install image of the computer is created.
Boot images
Boot images are the images with which you start a client computer before installing the operating system image. The boot image presents a boot menu that contains the images that users can install on their computers.
These images contain Windows PE 2.0 and the Windows Deployment Services client. You can use the default boot image included in the \ Sources directory of the Windows Server 2008 installation media (boot.wim).
This file must be only in advanced scenarios (for example, if you must add the image driver) to be changed. Important Only use the Boot.wim file on the Windows Server 2008 DVD.
If you boot.wim file to use on the Windows Vista DVD, you can not use all the functionality of Windows Deployment Services (for example, multicasting). There are also two image types that you can create from boot images:. Capture images and discover images.
Capture Images
Capture Images are boot images that allow the utility starts to record the Windows Deployment Services in place of the setup. If a reference computer (which has been prepared with Sysprep) start with a capture image, an install image of the reference computer is created and saved as a WIM file with an assistant. You can also create a medium (eg, CD, DVD or USB drive) that contains a capture image, and then boot a computer to the media. After you create the install image, you can use the image for PXE boot deployment Add the server. These images provide an alternative to command-line tool ImageX.exe.
Discover images
Discover images search images are boot images, which is enforced by that Setup.exe in Windows Deployment Services mode is started. Subsequently, a Windows Deployment Services server will be searched.
These images are typically used to deploy images to computers that are not configured for PXE or that are in networks where PXE is not allowed. If you create a discover image and apply it to the medium (eg, CD, DVD or Save USB drive), you can then boot a computer to the media.
The discover image on the media of the Windows Deployment Services server will be searched. The installation image is provided by the server for the computer. You can configure discover images so that a specific Windows Deployment Services server is used as a target. This means that you can create a discover image when a plurality of servers in your environment for each server and then can name each based on the name of the server.
QUESTION 534
Your corporate network includes an Active Directory Domain Services (AD DS) domain Lead2pass.com named.
The domain contains two Windows Server Update Services (WSUS) server with the name and WSUS1 WSUS2.
WSUS2 is a replica of WSUS1.
You must configure the Windows Server Update Services so that WSUS2 report sends data to WSUS1.
What you configure?
A. Update Reports
B. Synchronization Options
C. Computer Groups
D. Reporting rollup
Answer: D
QUESTION 535
Your network contains an Active Directory domain named contoso.com.
The domain contains a file server named Server1.
On Server1 the operating system Windows Server 2012 R2 is installed.
Check the RSoP of Server1.
The effective settings are shown in the picture (click on the button drawing).
You must ensure that an entry is recorded in the event log when it is on Server1 created or deleted a local user account.
How do you proceed?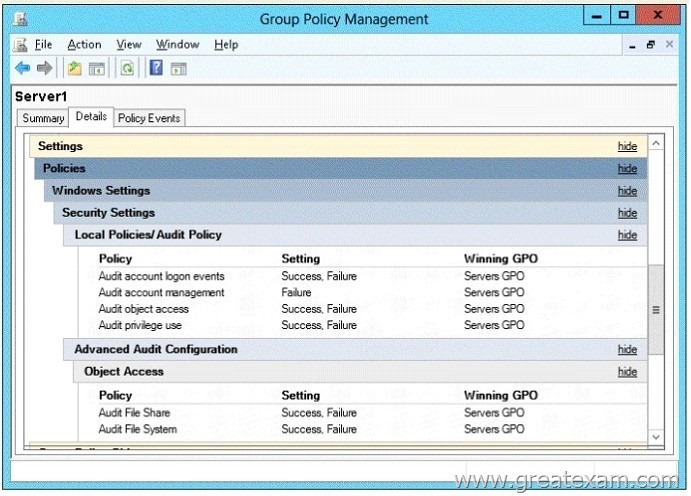
You need to ensure that an entry is added to the event log whenever a local user account is created or deleted on Server1.
What should you do?
A. Change the settings of the audit policy in Group Policy Object (GPO) ServersGPO
B. On Server1, attach a task to the security log.
C. Add the System log on Server1 a task.
D. Change the settings of the Advanced Audit Policy Configuration in Group Policy Object (GPO) ServersGPO
Answer: A
Explanation:
From the figure it is evident that the policy Audit account management is enabled only for failed attempts. Must be monitored in order to monitor the creation and deletion of accounts also successful attempts of account management. Audit account management is determined whether all Account Management events are monitored on a computer with this security setting.
The account management events include:
A user account or user group is created, changed or deleted.
A user account is renamed, disabled or enabled.
A password is set or changed.
If you define this policy setting, you can specify whether success or failure can be monitored and specify that the event type is not monitored. Success audits generate an audit entry is generated when any account management event succeeds. Failure audits generate an audit entry is generated when any account management event fails. If you “No monitoring” want to set this value to, activate the dialog “Properties” for this policy setting check box “Define these policy settings” and uncheck the checkbox “success” and “failure”.
When you use Advanced Audit Policy Configuration settings, you need to confirm that these settings are not overwritten by basic audit policy settings. The following procedure shows how to prevent conflicts by blocking the application of any basic audit policy settings.
Enabling Advanced Audit Policy Configuration
Basic and advanced audit policy configurations should not be mixed. As such, it’s best practice to enable Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings in Group Policy to make sure that basic auditing is disabled. The setting can be found under Computer Configuration\Policies\Security Settings\Local Policies\Security Options, and sets the SCENoApplyLegacyAuditPolicy registry key to prevent basic auditing being applied using Group Policy and the Local Security Policy MMC snap-in.
In Windows 7 and Windows Server 2008 R2, the number of audit settings for which success and failure can be tracked has increased to 53. Previously, there were nine basic auditing settings under Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\Audit Policy. These 53 new settings allow you to select only the behaviors that you want to monitor and exclude audit results for behaviors that are of little or no concern to you, or behaviors that create an excessive number of log entries. In addition, because Windows 7 and Windows Server 2008 R2 security audit policy can be applied by using domain Group Policy, audit policy settings can be modified, tested, and deployed to selected users and groups with relative simplicity.
Audit Policy settings
Any changes to user account and resource permissions.
Any failed attempts for user logon.
Any failed attempts for resource access.
Any modification to the system files.
Advanced Audit Configuration SettingsAudit compliance with important business-related and security-related rules by tracking precisely defined activities, such as:
A group administrator has modified settings or data on servers that contain finance information.
An employee within a defined group has accessed an important file. The correct system access control list (SACL) is applied to every file and folder or registry key on a computer or file share as a verifiable safeguard against undetected access.
In Servers GPO, modify the Audit Policy settings – enabling audit account management setting will generate events about account creation, deletion and so on.
Advanced Audit Configuration SettingsAdvanced Audit Configuration Settings ->Audit Policy -> Account Management -> Audit User Account Management
In Servers GPO, modify the Audit Policy settings – enabling audit account management setting will generate events about account creation, deletion and so on.
http://blogs.technet.com/b/abizerh/archive/2010/05/27/tracing-down-user-and-computer-account-deletion-in-active-directory.aspx
http://technet.microsoft.com/en-us/library/dd772623%28v=ws.10%29.aspx http://technet.microsoft.com/en-us/library/dd408940%28v=ws.10%29.aspx#BKMK_step2 http://technet.microsoft.com/en-us/library/jj852202(v=ws.10).aspx http://www.petri.co.il/enable-advanced-audit-policy-configuration-windows-server.htm
QUESTION 536
Your corporate network includes an Active Directory Domain Services (AD DS) domain contoso.local named.
On all servers Windows Server 2012 R2 is installed.
You want a read-only domain controller (RODC) to remove from the domain.
Which rule must be observed with respect to the removal RODC?
A. All read-only domain controllers must be removed from the domain before the last writable domain controller can be downgraded.
B. All writable domain controllers must be downgraded before a read-only domain controller can be removed from the domain.
C. The overall structure may contain only read-only domain controller.
D. There are no rules that must be followed when removing read-only domain controller.
Answer: A
Explanation:
A domain can not only read-only domain controller (RODC) included. A read-only domain controller (RODC) provide, you must deploy at least one writable domain controller for the same domain.
This serves as a replication partner for the RODC. Conversely, you must remove all read-only domain controller, bervor you demote the last writable domain controller.
QUESTION 537
On a server with the operating system Windows Server 2012 R2, you can uninstall the graphical shell for servers and get a server with minimal server user interface.
The user interface is similar to a minimal server installation Server with complete graphical user interface.
Some features are missing, however.
Which of the following features missing?
A. Microsoft Management Console (MMC)
B. Windows Explorer
C. Subset of the Control Panel
D. Server Manager
Answer: B
Explanation:
In Windows Ser1ver 2012, you can remove the server graphic shell, resulting in the “Minimal Server Interface”. This is similar to a server installation with a graphical user interface, but Internet Explorer 10, the Windows Explorer, the desktop and the Start screen are not installed.
The Microsoft Management Console (MMC), Server Manager, and a subset of the control panel are still available. If you start with a server installation with a graphical user interface, you can switch at any time using the Server Manager to minimum server user.
QUESTION 538
Which of the following features are available when Windows Server 2012 R2 is installed, although with complete graphical user interface but without the Desktop Experience feature presentation? (Select all that apply.)
A. Modern UI start screen
B. Integrated help system
C. Windows Search
D. Windows Media Player
Answer: AB
Explanation:
Using the Desktop Experience feature You can install a variety of Windows 8.1 features on a server running Windows Server 2012 Design. Thought this possibility is especially useful for providing remote desktop workstations. The Feature Desktop Experience includes uner including the Windows Media Player and Windows Search.
QUESTION 539
You administer a Windows Server 2012 R2 computer that is named Server1.
You want to use the Task Manager to end a running application.
Which register or which menu of Task Manager you use?
A. power
B. User
C. Options
D. Details
Answer: D
Explanation:
Running applications in Task Manager on the register details are terminated:
QUESTION 540
Your corporate network includes an Active Directory Domain Services (AD DS) domain contoso.local named.
Make the Windows Server Update Services (WSUS) on a server named Server1 ready.
You must prevent the Windows Server Update Services (WSUS) are automatically updated on Server1.
What step to run using the console Update Services?
A. Use the Products and Classifications options, configure the Products settings.
B. Use the Automatic Approvals options and change the settings on the tab Advanced.
C. Use the Option Products and Classifications and change the settings in the registry classifications.
D. Use the Automatic Approvals options and change the settings of the default rule for automatic approval.
Answer: B
Explanation:
In the advanced settings option rubberstamp approvals can be determined whether the updates that are intended for WSUS itself, are automatically approved. By default, this option is enabled.
All the 70-417 braindumps are updated. Get a complete hold of 70-417 PDF dumps and 70-417 practice test with free VCE player through GreatExam and boost up your skills.
http://www.greatexam.com/70-417-exam-questions.html