GreatExam 70-417 study guide provides you everything you will need to take your 70-417 exam. The 70-417 exam details are researched and produced by Professional Certification Experts who are constantly using industry experience to produce precise, and logical. You may get questions from different books, but logic is the key. Our Product will help you not only pass in the first try, but also save your valuable time.
QUESTION 501
Your network contains an Active Directory domain named contoso.com.
The domain contains 30 organizational units (OUs).
You need to ensure that a user named User1 can link Group Policy Objects (GPOs) in the domain.
What should you do?
A. From the Active Directory Users and Computers, add User1 to the Network Configuration Operators group.
B. From the Group Policies Management, click the contoso.com node and modify the Delegation settings.
C. From the Group Policies Management, click the Group policy Objects node and modify the Delegation settings.
D. From the Active Directory Users and Computers, add User1 to the Group Policy Creator Owners group.
Answer: B
Explanation:
In addition to the administrators of a domain by default, members of the Group Policy Creator Owners group the right to create group policies. If you want to enable users or groups to itself to create GPOs, then there is a path on their inclusion in the Group Policy Creator Owners group.
However, since the introduction of the Group Policy Management, there are other and more granular ways to delegate rights to manage GPOs. Thus, other groups or even individual users can now be equipped with these privileges. For this purpose you open the Group Policy Objects folder below the respective domain. Under the tab delegation is a list of all the groups and users who have the right to create GPOs. The button can add additional users are granted this privilege.
No matter how a user gets the right to create GPOs to, he may subsequently only edit or delete, which he himself has created those. Denied him thus remains the possibility to change already existing group policies or generally to link GPOs to an OU. For these tasks, users must be authorized separately.
The right to link GPOs can a user, as described in answer B, be granted.
QUESTION 502
Your network contains an Active Directory domain named contoso.com.
All client computers run Windows 8.
Your company has users who work from home. Some of the home users have desktop computers. Other home users have laptop computers.
All of the computers are joined to the domain.
All of the computer accounts are members of a group named Group1.
Currently, the home users access the corporate network by using a PPTP VPN.
You implement DirectAccess by using the default configuration and you specify Group1 as the DirectAccess client group.
The home users who have desktop computers report that they cannot use DirectAccess to access the corporate network.
The home users who have laptop computers report that they can use DirectAccess to access the corporate network.
You need to ensure that the home users who have desktop computers can access the network by using DirectAccess.
What should you modify?
A. The security settings of the computer accounts for the desktop computers
B. The membership of the RAS and IAS Servers group
C. The WMI filter for Direct Access Client Settings GPO
D. The conditions of the Connections to Microsoft Routing and Remote Access server policy
Answer: C
Explanation:
By default, the DirectAccess wizard DirectAccess prepared by applying a WMI filter on the GPO for the client settings for all laptops and notebook computers in the domain.
To apply the settings of the GPOs for DirectAccess clients on all the group CBRemotecomputer computer, we need to change or remove the WMI filter.
QUESTION 503
You have a Direct Access Server named Server1 running Server 2012.
You need to add prevent users from accessing websites from an Internet connection.
What should you configure?
A. Split Tunneling
B. Security Groups
C. Force Tunneling
D. Network Settings
Answer: C
Explanation:
If Direct Access is configured for Tunnelerzwingung, compounds of the DirectAccess client to the internal network and the Internet via the remote access server are routed. In the corporate network a proxy or a web filter can then be used, which blocks access to certain sites.
By default, the option is not enabled Tunnelerzwingung use.
The figure shows the default setting in the wizard for DirectAccess configuration:
QUESTION 504
Your network contains an Active Directory domain named contoso.com. The domain contains three domain controllers. The domain controllers are configured as shown in the following table.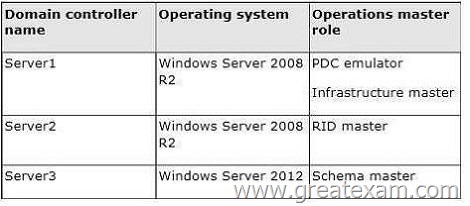
You are creating a Distributed File System (DFS) namespace as shown in the exhibit.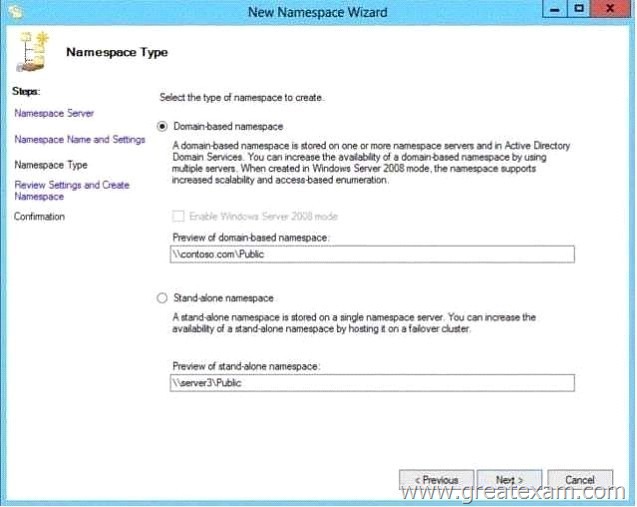
You need to identify which configuration prevents you from creating a DFS namespace in Windows Server 2008 mode.
Which configuration should you identify?
A. The location of the PDC emulator role
B. The functional level of the domain
C. The operating system on Server1 and Server3
D. The location of the RID master role
Answer: B
Explanation:
With DFS Namespaces (Distributed File System, Distributed File System) and the DFS Replication is simplified, enabling highly available access to files, load balancing and WAN-friendly replication. In the operating system Windows Server 2003 R2 Microsoft DFS Namespaces has (formerly known as DFS) revised and renamed, the DFS Management snap-in through the DFS Management snap-in replaces and introduced the new DFS Replication feature. In the operating system Windows Server 2008 Windows Server 2008 mode for domain-based namespaces as well as a number of improvements in terms of usability and performance have been added. With the DFS technologies WAN-friendly (Wide Area Network) replication and simplified, highly available access to geographically Distributed files allows. DFS includes these two technologies:
DFS Namespaces Using DFS Namespaces You can shared folders located on different servers, are grouped into one or more logically structured namespaces. Each namespace is displayed to users as a single shared folder with a series of subfolders. With this structure, the availability is increased, and for user connections to shared folders on the same Active Directory Domain Services site are automatically prepared, if it is available. Users are therefore not routed over WAN links.
DFS Replication DFS Replication is an efficient replication engine with multiple masters, with the folders between servers via network connections with limited bandwidth can be continuously synchronized. Thus, the FRS will File Replication Service (FRS) replaces a replication module for DFS Namespaces and for replication of the AD DS SYSVOL folder in domains that use the Windows Server 2008 domain functional level is used.
Domain-based namespaces in Windows Server 2008 mode
in Windows Server 2008 can domain-based namespaces in Windows Server 2008 mode are created. This support for access-based enumeration and increased scalability is activated. The 2000 Server introduced in Windows domain-based namespace is now referred to as “domain-based namespace (Windows 2000 Server mode).” To use the Windows Server 2008 mode, the domain and the domain-based namespace must meet the following minimum requirements:
For the domain, the Windows Server 2008 domain functional level is used.
On all namespace servers running Windows Server of 2008.
QUESTION 505
On the DFS replication your receive a wrap error on the sysvol on domain controller 4.
Which 3 steps should you do to recover this error in the correct order?
A. Stop FSR
B. Start FSR
C. Edit the computer object in AD
D. Edit the registry
E. Stop DFSR
F. Start DFRS
Answer: ABD
QUESTION 506
Your network contains an Active Directory domain named contoso.com. The domain functional level is Windows Server 2008. All domain controllers run Windows Server 2008 R2.
The domain contains a file server named Server1 that runs Windows Server 2012. Server1 has a BitLocker Drive Encryption (BitLocker)-encrypted drive.
Server1 uses a Trusted Platform Module (TPM) chip.
You enable the Turn on TPM backup to Active Directory Domain Services policy setting by using a Group Policy object (GPO).
You need to ensure that you can back up the BitLocker recovery information to Active Directory.
What should you do?
A. Raise the forest functional level to Windows Server 2008 R2.
B. Enable the Configure the level of TPM owner authorization information available to the operating system policy setting and set the Operating system managed TPM authentication level to None.
C. Add a BitLocker data recovery agent.
D. Import the TpmSchemaExtension.ldf and TpmSchemaExtensionACLChanges.ldf schema extensions to the Active Directory schema.
Answer: D
QUESTION 507
Your network contains an Active Directory domain named contoso.com.
The domain contains 2 WSUS servers, ServerA and ServerB.
ServerB is a replica server of ServerA.
You need to configure WSUS to report data from SERVERB to SERVERA.
What should you configure?
A. Update Reports
B. Synchronization
C. Computer Groups
D. Reporting Rollup
Answer: D
QUESTION 508
You are an admin. You have wsus with 2 sites which contain computers.
You want to have the ability to update the computers per site or together.
Which 3 steps do you do?
A. Create computer groups in wsus
B. Create synchronization options
C. Create GPO and configure updates
D. Under Tasks, click Synchronize now
Answer: ABC
QUESTION 509
Which of the options should you configure for a WDS pre-staged computer name?
You should select 2 of the 4 check boxes.
A. GUID o MAC-address preceding with nulls
B. WdsClientUnattend
C. Give the minimum required permission to a user who wants to promote a RODC.
D. ReferralServer
Answer: AC
QUESTION 510
You work as a network administrator at Lead2pass.com.
Lead2pass.com has an Active Directory Domain Services (AD DS) domain name Lead2pass.com.
All servers in the Lead2pass.com domain have Microsoft Windows Server 2012 R2 installed.
The computer accounts for all file servers are located in an organizational unit (OU) named DataOU. You are required to track user access to shared folders on the file servers.
Which of the following actions should you consider?
A. You should configure auditing of Account Logon events for the DataOU.
B. You should configure auditing of Object Access events for the DataOU.
C. You should configure auditing of Global Object Access Auditing events for the DataOU.
D. You should configure auditing of Directory Service Access events for the DataOU.
E. You should configure auditing of Privilege Use events for the DataOU.
Answer: B
QUESTION 511
You have installed Routing and Remote Access on Server1.
What should you configure next to use it as a NAT server?
A. Add New Interface
B. Create Static Route
C. Configure the IPv4 DHCP Relay Agent
D. Configure the IPv6 DHCP Relay Agent
Answer: A
QUESTION 512
Force an authoritative and non-authoritative synchronization for DFSR-replicated SYSVOL
A. dfsgui.msc
B. ultrasound
C. rplmon
D. frsutil
Answer: C
QUESTION 513
How to give the minimum required permission to a user who wants to promote a RODC.
A. member of the Domain Admins group
B. allowed to attach the server to the RODC computer account
C. Local admin
D. organization admin
Answer: BC
QUESTION 514
Your network contains an Active Directory domain named contoso.com.
The domain contains a member server named Server1. Server1 has the Web Server (IIS) server role installed.
On Server1, you install a managed service account named Service1.
You attempt to configure the World Wide Web Publishing Service as shown in the exhibit.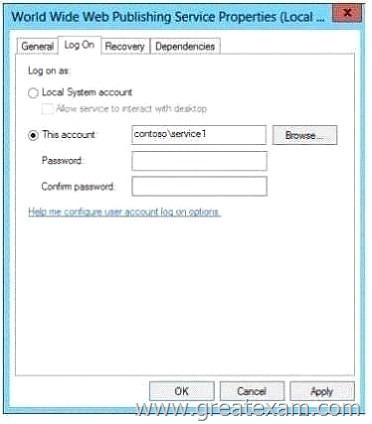
You receive the following error message:
“The account name is invalid or does not exist, or the password is invalid for the account name specified.”
You need to ensure that the World Wide Web Publishing Service can log on by using the managed service account.
What should you do?
A. Specify contoso\service1$ as the account name.
B. Specify [email protected] as the account name.
C. Reset the password for the account.
D. Enter and confirm the password for the account.
Answer: A
Explanation:
A managed service account is designed for service applications such as Internet Information Services, SQL Server, or Exchange to provide the following.:
– Automatic password management, so that these services can be separated from other services on the computer better.
– Simplified SPN management Service Principal Name (SPN) that allows
service administrators to set SPNs on these accounts. In addition, SPN
management can be delegated to other administrators.
Managed service accounts are created using PowerShell cmdlets and managed. The accounts are identified by a dollar sign at the end of the login name. After the logon name is correct, the settings are applied and the account will have the right to log on as a service given.
QUESTION 515
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2008 R2. The domain contains three servers that run Windows Server 2012.
The servers are configured as shown in the following table.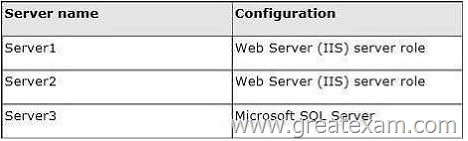
Server1 and Server2 are configured in a Network Load Balancing (NLB) cluster.
The NLB cluster hosts a website named Web1 that uses an application pool named App1.
Web1 uses a database named DB1 as its data store.
You create an account named User1.
You configure User1, as the identity of App1.
You need to ensure that contoso.com domain users accessing Web1 connect to DB1 by using their own credentials.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Configure the delegation settings of Server3.
B. Create a Service Principal Name (SPN) for User1.
C. Configure the delegation settings of User1.
D. Create a matching Service Principal Name (SPN) for Server1 and Server2.
E. Configure the delegation settings of Server1 and Server2.
Answer: BE
Explanation:
To enable impersonation to connect to the database server, the delegation settings for constrained delegation must (computer only trust for delegation to specified services) can be configured. Subsequently, the service principal name can be specified for the identity of the application pool as a delegate service.
The role of the service principal name to authenticate on SQL Server, if an application opens a connection and uses Windows authentication, passes the SQL Server Native Client to SQL Server computer name, -Instanznamen and optionally an SPN. If the connection passes an SPN, it is used without modification.
When the connection is no SPN, a default service principal name is created based on protocol, server name and instance name used. In both scenarios, the Service Principal Name is sent to the Key Distribution Center to a security token for retrieve authenticate the connection. If no security token can be retrieved using NTLM authentication.
A Service Principal Name (SPN, Service Principal Name) is the name that uniquely identifies a client about an instance of a service. The Kerberos authentication service can an SPN to authenticate a service use. When a client wants to connect to a service, it locates an instance of the service, posted an SPN for that instance, connects to the service and transfers the SPN to authenticate to the service.
The preferred method for authenticating users at SQL Server is Windows authentication. Clients that use Windows authentication to authenticate with NTLM or Kerberos. In an Active Directory environment, Kerberos authentication is always performed first. The Kerberos authentication for SQL Server 2005 clients that are using named pipes, not available.
QUESTION 516
Your network contains an Active Directory domain named contoso.com.
The domain contains a domain controller named DC4 that runs Windows Server 2012.
You create a DCCloneConfig.xml file.
You need to clone DC4.
Where should you place DCCloneConfig.xml on DC4?
A. %Systemroot%\SYSVOL
B. %Programdata%\Microsoft
C. %Systemroot%\NTDS
D. %Systemdrive%
Answer: C
QUESTION 517
Your network contains an Active Directory domain named contoso.com.
The domain contains a domain controller named DC1. On DC1, you add a new volume and you stop the Active Directory Domain Services (AD DS) service.
You run ntdsutil.exe and you set NTDS as the active instance.
You need to move the Active Directory database to the new volume.
Which Ntdsutil context should you use?
A. Configurable Settings
B. Partition management
C. IFM
D. Files
Answer: D
Explanation:
The Ntdsutil utility is used for using the Active Directory Domain Services (AD DS) and Active Directory Lightweight Directory Services (AD LDS).
It allows numerous tasks of maintenance. In order to Volume E both the database file and the associated log files in the directory NTDs: to move, you can successively make the following entries:
Ntdsutil
Activate Instance NTDS
Files
Move DB To E:\NTDS
Move Logs to e:\NTDS
The Ntdsutil utility contains numerous sub-programs:
QUESTION 518
Your network contains an Active Directory domain named adatum.com.
The domain contains a domain controller named DC1.
On DC1, you create a new volume named E.
You restart DC1 in Directory Service Restore Mode.
You open ntdsutil.exe and you set NTDS as the active instance.
You need to move the Active Directory logs to E:\NTDS\.
Which Ntdsutil context should you use?
A. IFM
B. Configurable Settings
C. Partition management
D. Files
Answer: D
Explanation:
A. Aids in modifying the time to live (TTL) of dynamic data that is stored in Active Directory Domain Services (AD DS).
At the configurable setting: prompt, type any of the parameters listed under Syntax.
B. Manages directory partitions for Active Directory Domain Services (AD DS) or Active Directory Lightweight Directory Services (AD LDS).
C. Creates installation media for writable (full) domain controllers, read-only domain controllers (RODCs), and instances of Active Directory Lightweight Directory Services (AD LDS).
D. ntdsutil move db to %s Moves the directory service log files to the new directory specified by %s, and updates the registry so that, upon service restart, the directory service uses the new location. http://technet.microsoft.com/en-us/library/cc753343(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/cc755229(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/cc730970(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/cc732530(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/cc753900(v=ws.10).aspx
QUESTION 519
The contoso.com domain contains 2 domain controllers running Server 2012, AD recycle bin is enabled for the domain.
DC1 is configured to take AD snapshots daily, DC2 is set to take snapshots weekly.
Someone deletes a group containing 100 users, you need to recover this group.
What should you do?
A. Authoritative Restore
B. Non Authoritative Restore
C. Tombstone Reanimation
D. Modify attribute is deleted
Answer: D
Explanation:
a new or significantly improved method for recovery of deleted Active Directory objects was introduced with Windows Server 2008 R2. If the Active Directory Recycle Bin is enabled in a forest, all attributes for a defined period (deletedObjectLifetime, DOL) are retained when you delete an object. Deleted Items can be restored without downtime of the domain controller and retaining all group memberships and permissions via LDAP editor or by using PowerShell cmdlets.
The Active Directory Recycle Bin can so far be considered a development of the tombstone reanimation, in which only the SID of an object is restored and the missing attributes are nachgepflegt example with the aid of an Active Directory snapshots. Deleted items are moved to the Deleted Objects container.
The container can not be displayed with the Active Directory Users and Computers or the ADSI Edit tool. To view the Deleted Objects container, you can use either LDP.exe or the Active Directory Explorer from Sysinternals.
With LDP.exe, the objects can also be restored equal by the boolean value of the attribute isDeleted for the deleted object from TRUE to FALSE is changed.
QUESTION 520
You have a RODC named Server1 running Server 2012.
You need to add a RODC Administrator.
How do you complete the task?
A. dsmgmt.exe
B. ntdsutil
C. Add user to Local Administrator Group on Server1
D. Use Security Group and modify RODC Delegated Administrator
Answer: D
Explanation:
A read-only domain controller (RODC) offers the possibility of dividing the Administrator role. This means that each domain user or security group can be used as a local administrator of an RODC without the user or group must be granted rights to the domain or other domain controllers.
A delegated administrator can log on to an RODC to maintenance work on the Server execute to update z. B. to a driver. The delegated administrator is not, however, be able to log on to another domain controller, or perform other administrative tasks in the domain. In this way, the effective management of RODCs a branch office to a security group from branch office users, instead of individual members of the Domain Admins group are delegated, without jeopardizing the safety of the rest of the domain. Before you install a read-only domain controller can in the wizard for making a account for a read-only domain controller, a user or a group Wreden defined as delegated RODC Administartor.
To grant a user or a group after you install a read-only domain controller local administrator rights for a read-only domain controller (RODC), the settings on the tab can Maintained by be configured in the properties of the computer account of RODC1. can open the Utilities dsmgmt and Ntdsutil for adding a delegated RODC administrator be used.
Microsoft recommends expressly that utilities dsmgmt and Ntdsutil not to be used for this purpose and instead specify a group which the Administrator Role Separation can be controlled.
The background is that the user, the password have been set with the help of dsmgmt or Ntdsutil as delegated RODC administrator can not be easily determined in retrospect.
The 70-417 PDF dumps and 70-417 practice test with free VCE player are available on GreatExam now. Get a complete hold of them through GreatExam to give your career a boost and start earning your Microsoft certification today!
http://www.greatexam.com/70-417-exam-questions.html