GreatExam presents the highest quality of 70-342 exam practice test which helps candidates to pass the 70-342 exams in the first attempt. GreatExam professional tools like questions and answers are extremely reliable source of preparation. When you use GreatExam preparation products your success in the Certification exam is guaranteed.
QUESTION 36
Drag and Drop Question
You restore the files of DB3 to EX3.
You need to mount DB3 on EX3. The solution must ensure that email messages sent to the users of DB3 while the database was offline are delivered once DB3 is mounted.
Which three actions should you perform in sequence? (To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.)
Answer: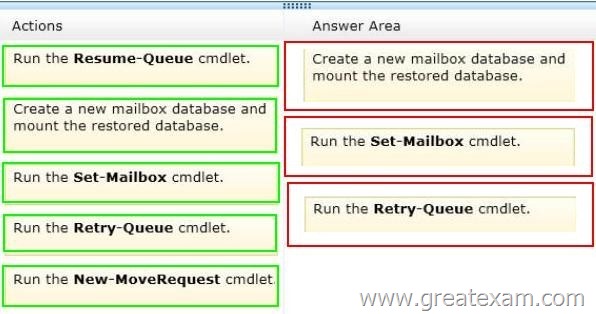
Explanation:
http://technet.microsoft.com/en-us/library/dd876926%28v=exchg.150%29.aspx
QUESTION 37
You need to implement a solution that meets the compliance requirements for the members of the legal department.
Which two cmdlets should you use? (Each correct answer presents part of the solution. Choose two.)
A. New-RoleAssignmentPolicy
B. Add-ManagementRoleEntry
C. New-ManagementRole Assignment
D. New-ManagementRole
E. New-ManagementScope
Answer: CE
Explanation:
* From scenario:
– Only the users in the legal department must be able to use eDiscovery to view the contents of email messages sent by the finance department users.
– Users in the legal department use a shared mailbox named Legal.
Legal is enabled for In- Place Hold. Legal is the only mailbox on DB2.
We need to assign the role to the legal department users using the New- ManagementRoleAssignment cmdlet.
To restrict the eDiscovery access to the finance users emails, we need to create a scope using the New-ManagementScope cmdlet.
Case Study 4: Proseware, Inc (QUESTION 38 ~ QUESTION 48)
Overview
General Overview
Proseware, Inc., is an international manufacturing company that has 1,000 users. Proseware has a sales department, a marketing department, a research department, and a human resources department. Proseware purchases another company named Contoso, Ltd. Contoso has 500 users.
Physical Locations
Proseware has two main offices located in New York and London.
The offices connect to each other by using a WAN link. Each office connects directly to the Internet.
Contoso has a single office in Dallas.
Existing Environment
Active Directory Environment
The Proseware network contains an Active Directory forest named proseware.com. The forest contains a single domain. All domain controllers run Windows Server 2012.
Each office contains three domain controllers. Each office is configured as an Active Directory site.
The Contoso network contains an Active Directory forest named contoso.com. The forest contains a single domain. All domain controllers run Windows Server 2012.
Exchange Server Organization
Proseware has an Exchange Server 2013 organization that contains four servers. The servers are configured as shown in the following table.
EX3 and EX4 are the members of a database availability group (DAG) named DAG1. DAG1 has two DAG networks. The networks are configured as shown in the following table.
Users connect to mail.proseware.com for Microsoft Outlook and Outlook Web App services. Mail.proseware.com resolves to an IP address on a hardware load balancer. All Outlook Anywhere users are enabled for Cached Exchange Mode.
Proseware pilots a hybrid deployment of Exchange Server 2013 and Microsoft Office 365. The mailbox of each pilot user is moved to Office 365. For the pilot mailboxes, all inbound email messages from the Internet are delivered to the Exchange Server organization, and then forwarded to Office 365.
Contoso has an Exchange Server 2010 organization.
Problem Statements
Proseware identifies the following issues:
– MapiNet is saturated with network traffic caused by the database replication between the members of DAG1 over MapiNet.
– The pilot users report that entries added to their Safe Senders list and their Blocked Senders list
fail to work.
– A recent power outage in the New York office prevents all users from accessing their mailbox.
– A user named User1 reports that email messages are being sent from her mailbox without her consent.
Requirements
Planned Changes
Proseware plans to implement the following changes:
– Several users at Contoso will use a mailbox at Proseware as their primary mailbox. The Contoso users will use Autodiscover to configure their client settings and will use single sign-on.
– For a special project, an IT administrator will create 20 distribution groups that will each contain 200 members.
– Certain users in both companies will have a ©contoso.com SMTP suffix as their primary email address.
Technical Requirements
Proseware identifies the following technical requirements for the Exchange Server organization:
– Internal email messages must be rejected if the messages cannot be protected by using Shadow Redundancy.
– All database replication between DAG1 members must occur over the Rep1Net network.
Site Resiliency Requirements
Proseware identifies the following site resiliency requirements for the Exchange Server organization:
– All mailboxes must be available if a single site becomes unavailable. The solution must not require administrator intervention.
– User traffic on the WAN links must be minimized.
Email Security Requirements
Proseware identifies the following requirements for securing email messages:
– Email recipients must be able to identify whether an email message was modified during delivery.
– All email messages stored in the mailbox databases must be protected from theft.
– Users must be able to encrypt email messages from Outlook Web App.
Retention Requirements
Proseware plans to reduce mailbox server storage usage and to limit company liability. Proseware identifies the following requirements:
– Email messages in the Deleted Items folder must be retained for only 30 days.
– Email messages in a mailbox folder named Projects must be retained for 540 days, unless the messages contain contractual information.
– Email messages in the Projects folder that contain contractual information must be retained indefinitely.
– All other email messages must be removed after one year.
QUESTION 38
Drag and Drop Question
You need to resolve the network traffic issue for MapiNet.
You suspend database replication.
Which three cmdlets should you run next in sequence?
(To answer, move the appropriate three cmdlets from the list of actions to the answer area and arrange them in the correct order.)
Answer: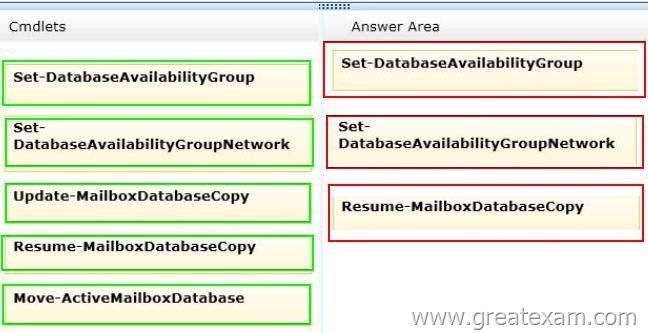
Explanation:
http://technet.microsoft.com/en-us/library/dd638104%28v=exchg.150%29.aspx
QUESTION 39
Drag and Drop Question
You are preparing the environment for the planned retention solution.
You need to identify which policy tags must be created to meet the retention requirements.
Which policy tag types should you identify? (To answer, drag the appropriate policy tag types to the correct message types. Each policy tag tag may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)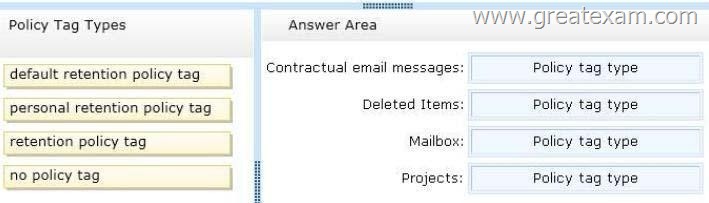
Answer: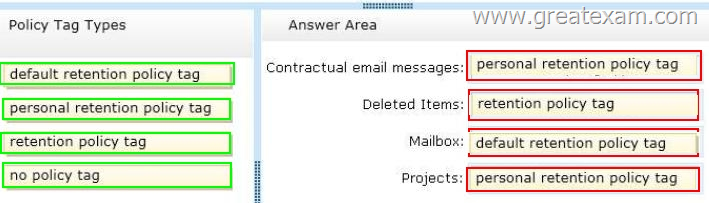
Explanation:
Contractual email messages – Personal retention policy tags apply to individual items such as email messages
Deleted items – Retention Policy Tags are created for default folders such as Inbox, Deleted items, etc.
Mailbox – Default Policy Tags apply to all items if they are not tagged
Projects – Personal retention policy tags apply settings to custom folders
http://technet.microsoft.com/en-us/library/dd297955(v=exchg.150).aspx
QUESTION 40
Drag and Drop Question
You need to implement UM for the sales department users.
Which four commands should you run in sequence? (To answer, move the appropriate four commands from the list of commands to the answer area and arrange them in the correct order.)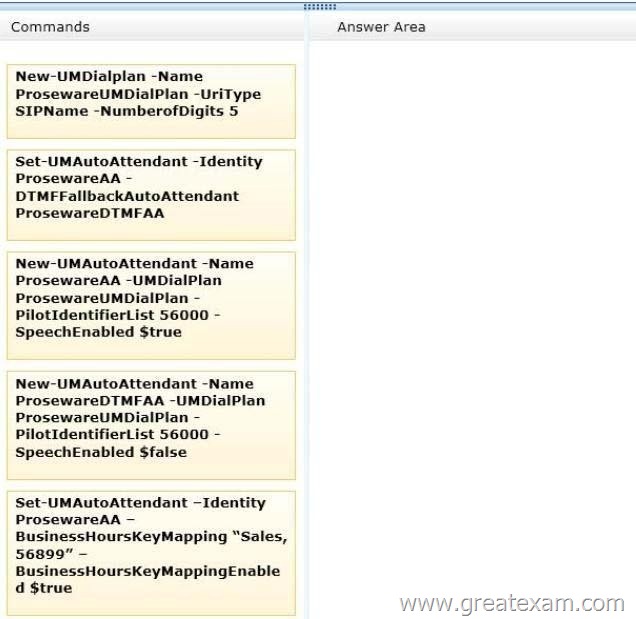
Answer: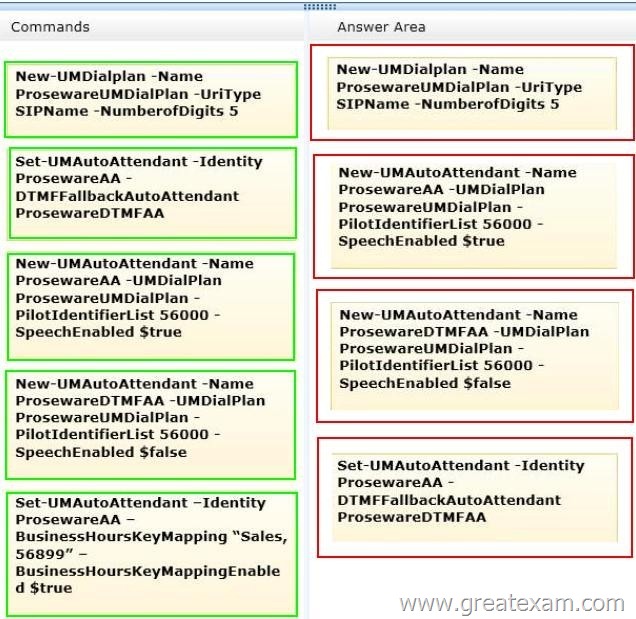
Explanation:
http://technet.microsoft.com/en-us/library/jj673564(v=exchg.150).aspx
QUESTION 41
You are evaluating the deployment of two additional Client Access servers and a hardware load balancer in the London office.
You need to recommend changes to the Client Access namespace design to meet the site resiliency requirements.
Which three actions should you recommend?
(Each correct answer presents part of the solution. Choose three.)
A. In the London office, set mail.proseware.com as the external host name for Outlook Anywhere.
In the New York office, set mail.proseware.com as the external host name for Outlook Anywhere.
B. In the London office, set ionmail.proseware.com as the internal host name for Outlook Anywhere.
In the New York office, set nycmail.proseware.com as the internal host name for Outlook Anywhere.
C. Use DNS round robin for the external host name for Outlook Anywhere.
D. Use DNS round robin for the internal host name for Outlook Anywhere.
E. In the London office, set nycmail.proseware.com as the external host name for Outlook Anywhere.
In the New York office, set ionmail.proseware.com as the external host name for Outlook Anywhere.
F. In the London office, set mail.proseware.com as the internal host name for Outlook Anywhere.
In the New York office, set mail.proseware.com as the internal host name for Outlook Anywhere.
Answer: ABC
Explanation:
A: Use mail.proseware.com as the external host name for Outlook Anywhere at both locations.
B: Use internal names (lonmail.proseware.com and nycmail.proseware.com) as the internal host name for Outlook Anywhere in London and New York respectively.
C: To meet the resiliency requirement use the external host name (mail.proseware.com) for DNS round robin for Outlook anywhere.
* From scenario:
/ Users connect to mail.proseware.com for Microsoft Outlook and Outlook Web App services. Mail.proseware.com resolves to an IP address on a hardware load balancer.
/ All Outlook Anywhere users are enabled for Cached Exchange Mode.
/ Proseware has two main offices located in New York and London.
/
Site Resiliency Requirements
– All mailboxes must be available if a single site becomes unavailable. The solution must not require administrator intervention.
– User traffic on the WAN links must be minimized.
* Split DNS for Exchange Server 2013
Split DNS allows your internal clients to receive a different answer to their DNS lookups than an external client would receive. In effect you have your Exchange namespace hosted on your internal DNS server, with records configured to point to internal IP addresses.
QUESTION 42
You need to recommend a solution to meet the technical requirements for redundancy during email delivery.
Which cmdlet should you include in the recommendation?
A. Set-FrontendTransportService
B. Set-TransportConfig
C. Set-MailboxTransportService
D. Set-TransportService
Answer: B
Explanation:
Internal email messages must be rejected if the messages cannot be protected by using
Shadow Redundancy.
We need to use the Set-TransportConfig cmdlet with the RejectMessageOnShadowFailure
parameter.
QUESTION 43
Hotspot Question
You need to recommend which technology can be used to meet each email security requirement.
What should you recommend? (To answer, select the appropriate technology for each requirement in the answer area.)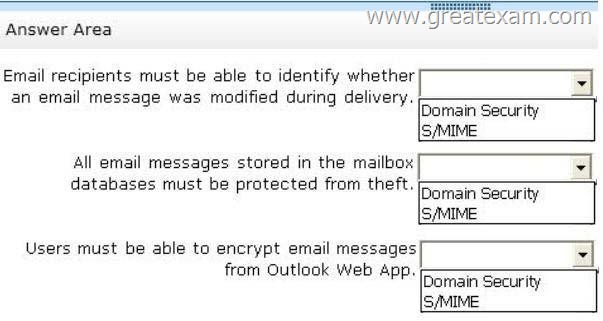
Answer: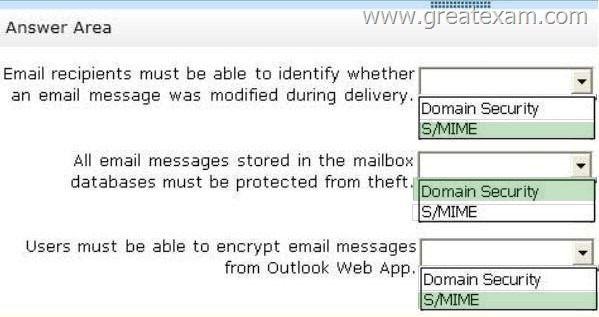
Explanation:
To Encrypt OWA E-mails, S/MIME is required. This is not related to Domain Security.
https://support.quovadisglobal.com/KB/a287/how-do-i-enable-smime-control-to-digital-sign-encrypt.aspx
http://blogs.technet.com/b/mconeill/archive/2013/08/29/outlook-2013-vs-owa-2013.aspx
QUESTION 44
Drag and Drop Question
You need to recommend a solution to support the planned changes for the integration of the Exchange Server organizations of Contoso and Proseware.
What should you configure in each organization? (To answer, drag the appropriate objects to the correct forests. Each object may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)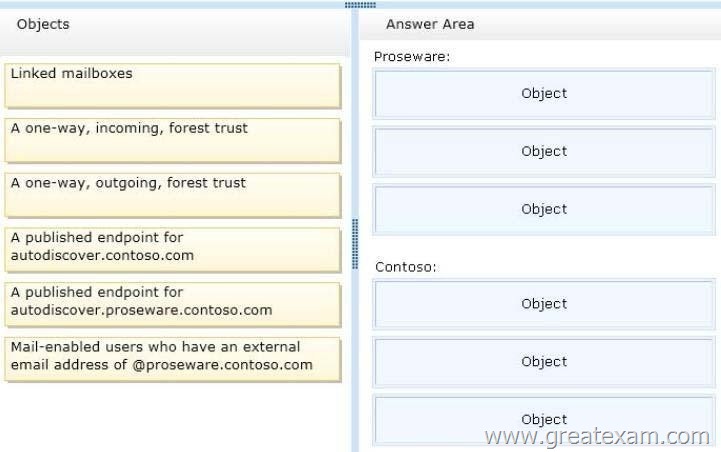
Answer: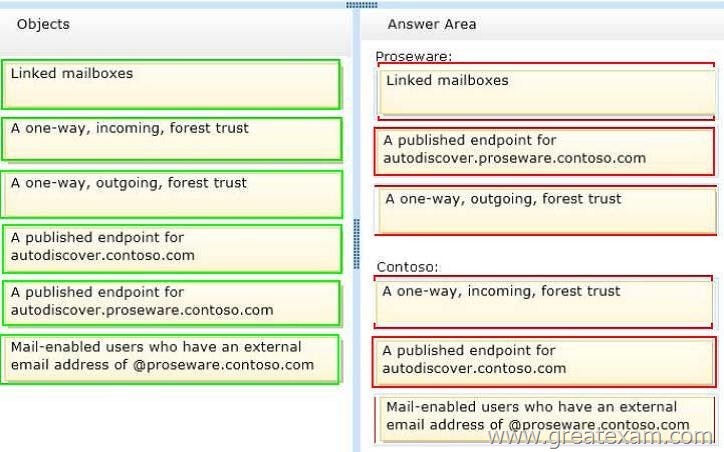
QUESTION 45
You need to resolve the content filtering issue for the Office 365 pilot users.
What should you do?
A. Run the Set-Mailbox cmdlet and specify the -MaxBiockedSenders and the -MicrosoftOnlineServicesID parameters.
B. Run the Microsoft Online Services Directory Synchronization Configuration Wizard and select Enable Exchange hybrid deployment.
C. Modify the default content filter policy from the Office 365 portal.
D. Run the Set-Mailbox cmdlet and specify the -MaxSafeSenders and the -MicrosoftOnlineServicesIDparameters.
Answer: B
Explanation:
* Scenario:
/ The pilot users report that entries added to their Safe Senders list and their Blocked Senders list fail to work.
/ For the pilot mailboxes, all inbound email messages from the Internet are delivered to the Exchange Server organization, and then forwarded to Office 365.
* Hybrid Configuration wizard Exchange 2013 includes the Hybrid Configuration wizard which provides you with a streamlined process to configure a hybrid deployment between on-premises Exchange and Exchange Online organizations.
QUESTION 46
Hotspot Question
You need to recommend a solution to audit the issue of User1.
Which command should you recommend? (To answer, select the appropriate options in the answer area.)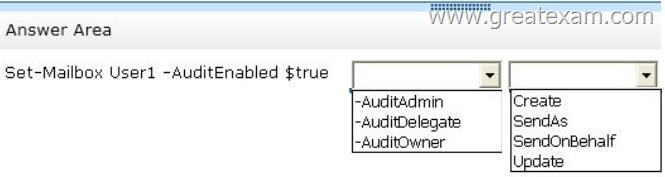
Answer: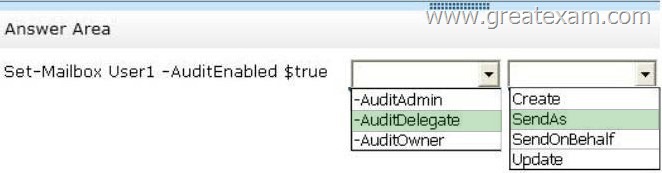
Explanation:
http://technet.microsoft.com/en-us/library/bb123981(v=exchg.150).aspx
http://technet.microsoft.com/en-us/library/bb676368(v=exchg.141).aspx
QUESTION 47
You discover that the Large Audience MailTip is not displayed when users compose an email message to the 20 new distribution groups.
You need to ensure that the Large Audience MailTip is displayed for the new distribution groups immediately.
Which cmdlet should you use?
A. Set-DistributionGroup
B. Set-MailboxServer
C. Set-ClientAccessServer
D. Start-ManagedFolderAssistant
Answer: B
Explanation:
We need to use the Set-MailboxServer cmdlet with the ForceGroupMetricsGeneration parameter to force a count of the number of members of the distribution groups.
The ForceGroupMetricsGeneration parameter specifies that group metrics information must be generated on the Mailbox server regardless of whether that server generates an offline address book (OAB). By default, group metrics are generated only on servers that generate OABs.
Group metrics information is used by MailTips to inform senders about how many recipients their messages will be sent to.
You need to use this parameter if your organization doesn’t generate OABs and you want the group metrics data to be available.
http://technet.microsoft.com/en-us/library/jj674302(v=exchg.150).aspx
QUESTION 48
Hotspot Question
You need to recommend a solution to audit the issue of User1.
Which command should you recommend? (To answer, select the appropriate options in the answer area.)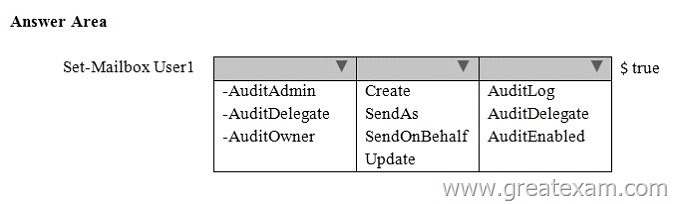
Answer: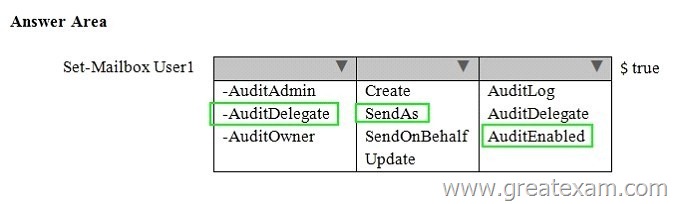
QUESTION 49
Drag and Drop Question
You have an Exchange Server 2013 organization that has Information Rights Management (IRM) configured.
Users report that they cannot apply IRM protection to email messages from Outlook Web App.
You verify that the users can protect the messages by using IRM from Microsoft Outlook.
You need to recommend a solution to ensure that the users can protect email messages by using IRM from Outlook Web App.
Which four actions should you recommend? To answer, move the four appropriate actions from the list of actions to the answer area and arrange them in the correct order.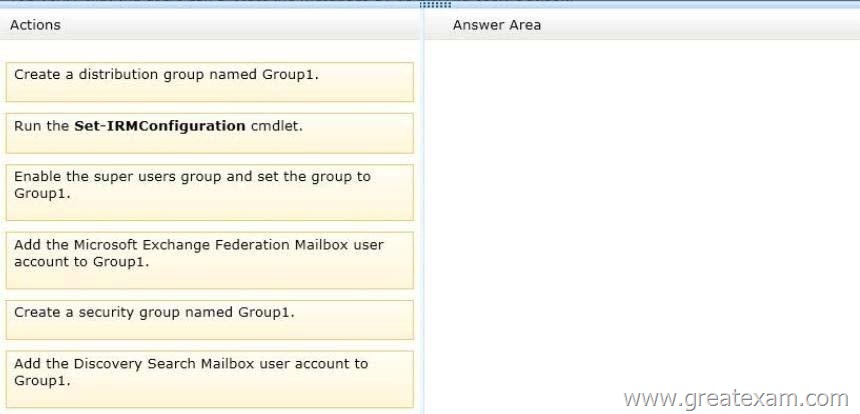
Answer: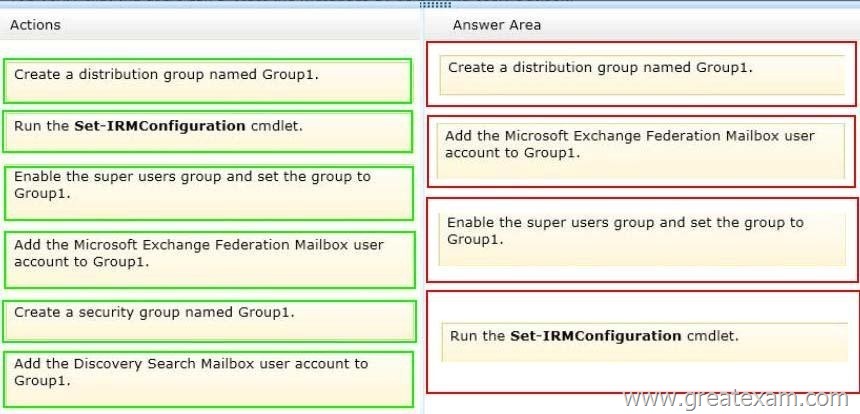
Explanation:
Box 1: Create a distribution group named Group1.
Box 2: Add the Microsoft Exchange Federation Mailbox user account to Group1.
Box 3: Enable the super users group and set the group to Group1.
Box 4: Run the Set-IRMConfiguration cmdlet.
Note:
* To enable IRM in Outlook Web App, you must add the Federation mailbox, a system mailbox created by Exchange 2013 Setup, to the super users group in AD RMS.
* Step 1: Use the Shell to add the Federation mailbox to a distribution group If a distribution group has been created and configured as a super users group in the AD RMS cluster, you can add the Exchange 2013 Federation mailbox as a member of that group. If a super users group isn’t configured, you must create a distribution group and add the Federation mailbox as a member.
1.Create a distribution group dedicated for use as an AD RMS super users group.
2. Add the user FederatedEmail.4c1f4d8b-8179-4148-93bf-00a95fa1e042 to the new distribution group.
Step 2: Use AD RMS to set up a super users group
Perform the following procedure on an AD RMS cluster. The account used to perform this procedure must be a member of the AD RMS Enterprise Administrators local group on the AD RMS server.
1. Open the Active Directory Rights Management Services console and expand the AD RMS cluster.
2. In the console tree, expand Security Policies, and then click Super Users.
3. In the action pane, click Enable Super Users.
4. In the result pane, click Change Super User Group to open the Super Users property sheet.
5. In the Super user group box, type the email address of the distribution group you created in the previous procedure, or click Browse to select a distribution group.
* Information workers increasingly use e-mail to exchange sensitive information. To help secure this information, organizations can use Information Rights Management (IRM) to apply persistent protection to messaging content. Prior to Microsoft Exchange Server 2010, effective use of IRM protection was limited to Outlook clients. In Exchange Server 2007, Microsoft Outlook Web Access users were required to download the Rights Management add-in for Microsoft Internet Explorer so they could access IRM-protected content.
In Exchange 2013, IRM in Outlook Web App allows your users to access the rich IRM functionality offered by Exchange to apply persistent IRM-protection to messaging content.
Reference: Information Rights Management in Outlook Web App
Reference: Add the Federation Mailbox to the AD RMS Super Users Group
QUESTION 50
Contoso, Ltd., and Fabnkam, Inc., are partner companies.
Each company has an Exchange Server 2013 organization in a data center that is connected to the Internet. All of the Exchange servers in both of the organizations have the Client Access server role and the Mailbox role installed.
The data centers connect to each other by using a redundant high-speed WAN link.
The following mail exchanger (MX) records are configured:
– Contoso.com MX 10 mail.contoso.com
– Fabrikam.com MX 10 mail.fabrikam.com
You need to recommend a solution for inbound mail flow.
The solution must meet the following requirements:
– Users in both companies must receive email from the Internet if either of the Internet links fails.
– Mail from the Internet to contoso.com must be received by mail.contoso.com if the Internet link at the Contoso data center is available.
– Mail from the Internet to fabrikam.com must be received by mail.fabrikam.com if the Internet link at the Fabrikam data center is available.
Which two actions should you recommend? (Each correct answer presents part of the solution. Choose two.)
A. Create the following DNS records:
Contoso.com MX 20 mail.fabrikam.com
Fabrikam.com MX 20 mail.contoso.com
B. Create the following DNS records:
Contoso.com MX 10 mail.fabrikam.com
Fabrikam.com MX 10 mail.contoso.com
C. For each organization, configure an internal relay domain and a Send connector.
D. For each organization, configure an external relay domain and a Receive connector.
E. Create the following DNS records:
Contoso.com MX 5 mail.fabrikam.com
Fabrikam.com MX 5 mail.contoso.com
Answer: AC
Explanation:
A: Use a priority above 10.
C:
* When you configure an internal relay domain, some or all of the recipients in this domain don’t have mailboxes in this Exchange organization. Mail from the Internet is relayed for this domain through Transport servers in this Exchange organization.
* An organization may have to share the same SMTP address space between two or more different messaging systems. For example, you may have to share the SMTP address space between Exchange and a third-party messaging system, or between Exchange environments that are configured in different Active Directory forests. In these scenarios, users in each email system have the same domain suffix as part of their email addresses. To support these scenarios, you need to create an accepted domain that’s configured as an internal relay domain.
You also need to add a Send connector that’s sourced on a Mailbox server and configured to send email to the shared address space. If an accepted domain is configured as authoritative and a recipient isn’t found in Active Directory, a non- delivery report (NDR) is returned to the sender. The accepted domain that’s configured as an internal relay domain first tries to deliver to a recipient in the Exchange organization. If the recipient isn’t found, the message is routed to the Send connector that has the closest address space match.
Incorrect:
D: When you configure an external relay domain, messages are relayed to an email server that’s outside your Exchange organization and outside the organization’s network perimeter.
http://technet.microsoft.com/en-us/library/bb124423%28v=exchg.150%29.aspx#BKMK_InternalRelayDomains
QUESTION 51
Drag and Drop Question
You have an Exchange Server 2013 database availability group (DAG). Each member of the DAG has two network interfaces named Network1 and Network2. Network1 is used for client connections. Network2 is used for database replication.
Network2 fails.
You discover that replication traffic is sent over Network1.
You need to ensure that all of the database replication traffic is sent over Network2.
The solution must minimize database replication downtime.
Which three actions should you perform? To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the correct order.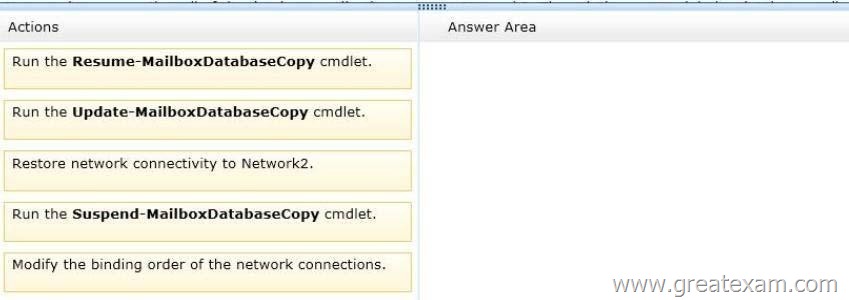
Answer: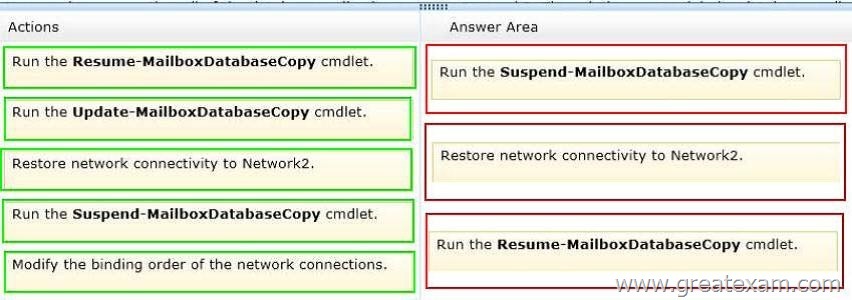
Explanation:
Box 1: Run the Suspend-MailboxDatabaseCopy cmdlet.
Box 2: Restore the connectivity to Network2.
Box 3: Run the Resume-MailboxDatabaseCopy cmdlet.
Note:
* You may need to suspend or resume a database copy for a variety of reasons, such as maintenance on the disk that contains a database copy, or suspend an individual database copy from activation for disaster recovery purposes.
This example suspends continuous replication for a copy of the database DB1 hosted on the server MBX1. An optional comment has also been specified.
Suspend-MailboxDatabaseCopy -Identity DB1\MBX1 -SuspendComment “Maintenance on MBX1” – Confirm:$False
This example resumes a copy of the database DB1 on the server MBX1.
Resume-MailboxDatabaseCopy -Identity DB1\MBX1
Reference: Suspend or Resume a Mailbox Database Copy
QUESTION 52
You have an Exchange Server 2013 organization that contains two servers.
The servers are configured as shown in the following table.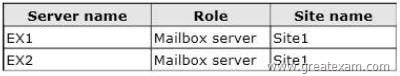
EX1 and EX2 are members of a database availability group (DAG) named DAG1.
You have a database named DB1 that replicates to EX1 and EX2. EX1 fails.
You discover that DB1 does not mount on EX2.
You view the status of the mailbox databases as shown in the following table.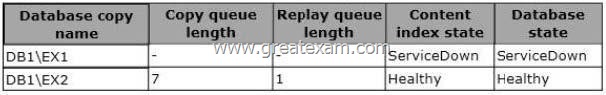
You need to ensure that the database attempts to mount on EX2 if EX1 fails.
What should you change?
A. The AutoDatabaseMountDial setting to Lossless
B. The AutoDatabaseMountDial setting to BestAvailabilty
C. The activation preference of DB1\EX2
D. The activation preference of DB1\EX1
Answer: B
Explanation:
* The MailboxServer.AutoDatabaseMountDial property gets or sets the automatic database mount behavior for an Exchange server that is running the Mailbox server role in a continuous replication environment after a database failover.
* The AutoDatabaseMountDial property specifies the automatic database mount behavior of a Mailbox server after a failover. Each behavior is based on the copy queue length, or the number of logs that are recognized by the passive copy that need to be replicated. If the copy queue length is greater than the value specified for the behavior, the database does not automatically mount. If the copy queue length is less than or equal to the value specified for the behavior, the Mailbox server tries to copy the remaining logs to the passive copy and mounts the database.
* BestAvailability
The database automatically mounts immediately after a failover if the queue length is less than or equal to 12.
Incorrect:
Not A: Lossless
The database does not automatically mount until all logs generated on the active device are copied to the passive device
http://msdn.microsoft.com/en-us/library/microsoft.exchange.data.directory.management.mailboxserver.autodatabasemountdial%28v=exchg.150%29.aspx
QUESTION 53
Your company has a data center in New York and a data center in Miami.
The company has an Exchange Server 2013 organization that contains a database availability group (DAG).
The DAG contains servers in both data centers.
The company plans to deploy Outlook Anywhere to all users.
You configure the following:
– All of the Exchange Server 2013 virtual directories in the New York data center use a host name of mail.contoso.com.
– All of the Exchange Server 2013 virtual directories in the Miami data center use a host name of miami.mail.contoso.com.
– In each data center, a certificate from an enterprise certification authority (CA) is configured to contain the following:
– A certificate principal name of mail.contoso.com
– Subject alternate names of mail.contoso.com and miami.mail.contoso.com
You need to recommend which task must be performed to meet the following requirements:
– Users always must attempt to connect first to a server in the data center where their mailbox is located.
– Users must be able to access their mailbox if a single data center fails.
What should you recommend?
A. Change the external host name of the Miami data center to mail.contoso.com.
B. Modify the ExternalUrl of the Autodiscover virtual directory of the Client Access servers.
C. Run the Set-OutlookProvider cmdlet.
D. Run the Add-AvailabilityAddressSpace cmdlet.
Answer: B
Explanation:
http://technet.microsoft.com/en-us/library/bb123683%28v=exchg.150%29.aspx
Use the Set-OutlookProvider cmdlet to set specific global settings using the msExchOutlookProvider attribute on the msExchAutoDiscoverConfig object in Active Directory.
A – wrong because that would only confuse the DNS resolution and not allow clients to connect to their site
B – Correct this is the only answer that specifies an external URL specific to each site
C – wrong because the Set-OutlookProvider cmdlet is Organization wide and not site-specific
D – wrong because this deals with free/busy information and not Outlook Anywhere connectivity
QUESTION 54
Your company has offices in Tokyo, Bangkok, and Shanghai.
All connections to the Internet are routed through an Internet connection in the Tokyo office. All of the offices connect to each other by using a WAN link.
The network contains 10 servers that have Exchange Server 2010 installed.
The servers are configured as shown in the following table.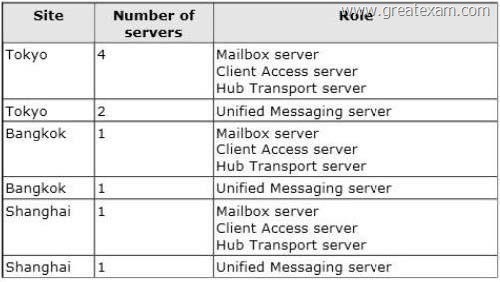
You plan to deploy 10 servers that will have Exchange Server 2013 installed.
The servers will be configured as shown in the following table.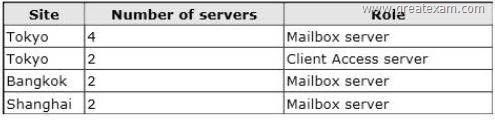
Each site has an IP-PBX that provides telephony services for the mailboxes in that site by using unsecured SIP over TCP 5070. The IP-PBX uses the same port to connect to multiple SIP peers.
You need to recommend which tasks must be performed to ensure that the Unified Messaging (UM) features are available to the mailboxes if a single server fails.
Which three actions should you include in the recommendation? (Each correct answer presents part of the solution. Choose three.)
A. Configure the Exchange Server 2013 Mailbox servers to listen to unsecured SIP on TCP 5070.
B. Configure the Exchange Server 2013 Client Access servers to listen to unsecured SIP on TCP 5070.
C. Install the Client Access server role on the Exchange Server 2013 servers in the Shanghai and Bangkok offices.
D. Configure the Exchange Server 2013 Mailbox servers as additional SIP peers that contain new pilot identifiers.
E. Configure the Exchange Server 2013 Client Access servers as additional SIP peers that contain new pilot
identifiers.
Answer: BCE
Explanation:
Note:
* Exchange 2013 Unified Messaging offers administrators:
/ A complete voice mail system
Unified Messaging offers a complete voice mail solution using a single store, transport, and directory infrastructure. The store is provided by a Mailbox server and forwarding of incoming calls from a VoIP gateway or IP PBX is handled by a Client Access server.
All email and voice mail messages can be managed from a single management point, using a single administration interface and tool set.
/ An Exchange security model
The Microsoft Exchange Unified Messaging service on a Mailbox server and the Microsoft
Exchange Unified Messaging Call Router service on a Client Access server run as a single
Exchange server account.
Consolidation
* The client access server (CAS) is a server role that handles all client connections to Exchange Server 2010 and Exchange 2013. The CAS supports all client connections to Exchange Server from Microsoft Outlook and Outlook Web App, as well as ActiveSync applications. The CAS also provides access to free/busy data in Exchange calendars.
The CAS is one of five server roles in Exchange Server 2007 and Exchange 2010, and one of two server roles in Exchange Server 2013. It must be installed in every Exchange Server organization and on every Active Directory (AD) site that has the Exchange mailbox server role installed.
QUESTION 55
You have an Exchange Server organization that contains five servers.
The servers are configured as shown in the following table.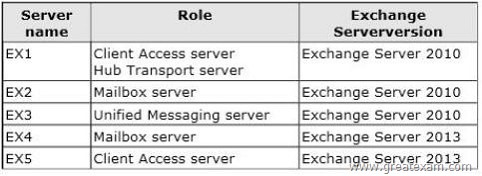
You need to create a Lync Server SIP Unified Messaging (UM) dial plan to enable voice integration between Lync Server and Exchange Server.
Which three Exchange servers should you associate to the UM dial plans? (Each correct answer presents part of the solution. Choose three.)
A. EX1
B. EX2
C. EX3
D. EX4
E. EX5
Answer: CDE
Explanation:
C: You can enable Unified Messaging (UM) in Microsoft Exchange Server 2010.
You must enable the Exchange computer running the Unified Messaging server role before the Unified Messaging server can process calls for UM-enabled Exchange 2010 recipients in your Exchange organization. However, the Unified Messaging server also must be added to a UM dial plan before it can process calls for Unified Messaging.
D,E:
* Requirements and Recommendations
Client Access and Mailbox. In Microsoft Exchange Server 2013, Exchange UM runs as a service on these servers.
* Deploy the Exchange Mailbox server roles in each Exchange Unified Messaging (UM) forest where you want to enable users for Exchange UM.
http://technet.microsoft.com/en-us/library/aa996399%28v=exchg.150%29.aspx
GreatExam is now here to help you with your 70-342 exam certification problems. Because we are the best 70-342 exam questions training material providing vendor, all of our candidates get through 70-342 exam without any problem.
http://www.greatexam.com/70-342-exam-questions.html