GreatExam gives the latest, authoritative and complete 70-417 braindumps for 70-417 exam, because of that, all of our candidates pass 70-417 certification without any problem. The biggest feature is the regular update of 70-417 PDF and VCE, which keeps our candidates’ knowledge up to date and ensures their 70-417 exam success.
QUESTION 361
Drag and Drop Question
You have a server that runs Windows Server 2012 R2.
You need to create a volume that will remain online if two disks in the volume fail.
The solution must minimize the number of disks used to create the volume.
Which three actions should you perform in sequence? (To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.)
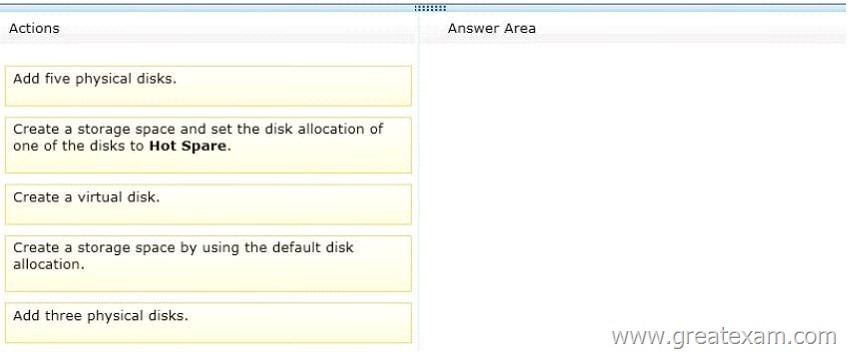
Answer: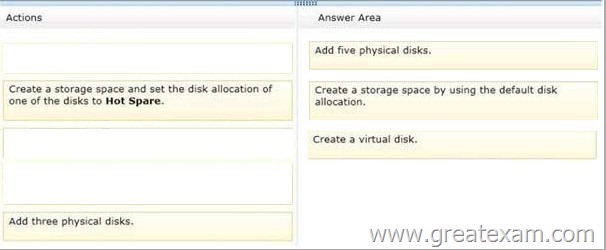
Explanation:
http://www.mustbegeek.com/configure-storage-space-in-server-2012/
QUESTION 362
Your network contains an Active Directory domain named contoso.com.
You install Windows Server 2012 R2 on a new server named Server1 and you join Server1 to the domain.
You need to ensure that you can view processor usage and memory usage information in Server Manager.
What should you do?
A. From Server Manager, click Configure Performance Alerts.
B. From Performance Monitor, create a Data Collector Set (DCS).
C. From Performance Monitor, start the System Performance Data Collector Set (DCS).
D. From Server Manager, click Start Performance Counters.
Answer: D
Explanation:
You should navigate to the Server Manager snap-in and there click on All Servers, and then Performance Counters. The Performance Counters, when started can be set to collect and display data regarding processor usage, memory usage, amongst many other resources like disk-related and security related data, that can be monitored.
http://technet.microsoft.com/en-us/library/bb734903.aspx
QUESTION 363
Hotspot Question
Your network contains two servers named Server1 and Server2 that run Windows Server 2012 R2. Server1 has the Hyper-V server role installed. Server2 has the Windows Deployment Services server role installed.
On Server1, you have a virtual machine named VM1.
You plan to deploy an image to VM1 by using Windows Deployment Services (WDS).
You need to ensure that VM1 can connect to Server1 by using PXE.
Which settings should you configure on VM1?To answer, select the appropriate settings in the answer area.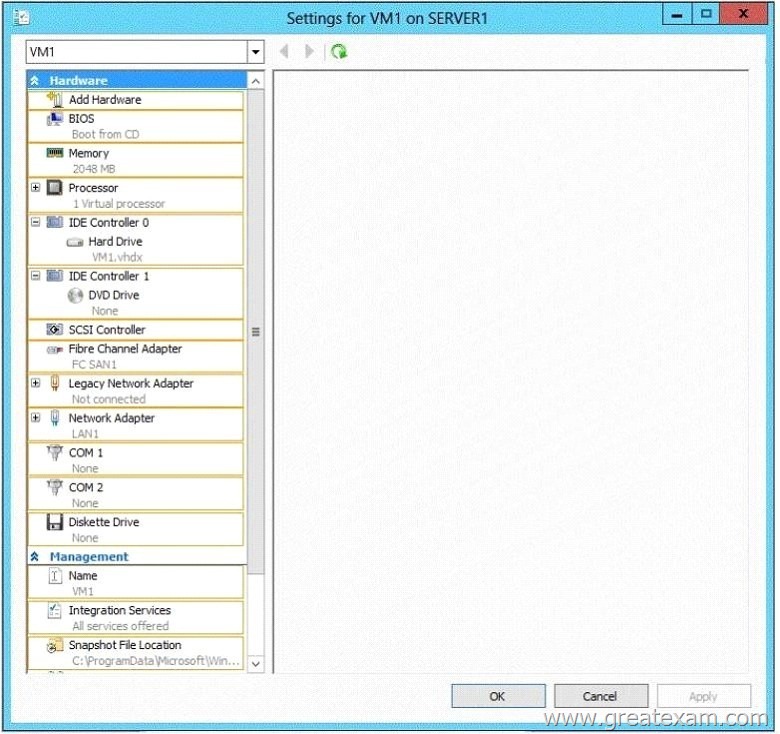
Answer: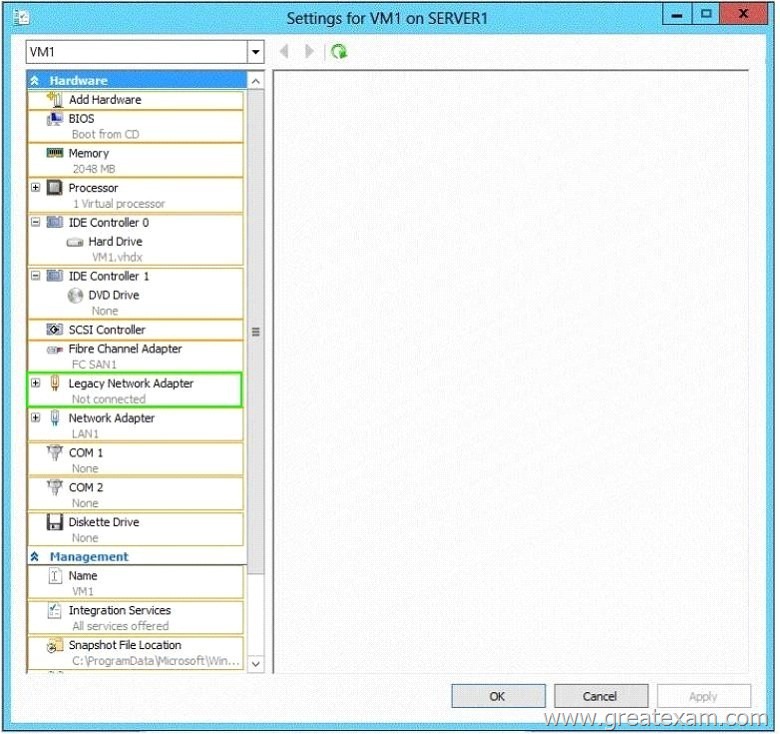
QUESTION 364
Your network contains an Active Directory domain named contoso.com. The domain contains a member server named HVServer1. HVServer1 runs Windows Server 2012 R2 and has the Hyper-V server role installed.
HVServer1 hosts 10 generation 1 virtual machines. All of the virtual machines connect to a virtual switch named Switch1. Switch1 is configured as a private network. All of the virtual machines have the DHCP guard and the router guard settings enabled.
You install the DHCP server role on a virtual machine named Server1.
You authorize Server1 as a DHCP server in contoso.com. You create an IP scope.
You discover that the virtual machines connected to Switch1 do not receive IP settings from Server1.
You need to ensure that the virtual machines can use Server1 as a DHCP server.
What should you do?
A. Enable MAC address spoofing on Server1.
B. Enable single-root I/O visualization (SR-IOV) on Server1.
C. Disable the DHCP guard on Server1.
D. Disable the DHCP guard on all of the virtual machines that are DHCP clients.
Answer: C
Explanation:
DHCP guard setting
This setting stops the virtual machine from making DHCP offers over this network interface. To be clear this does not affect the ability to receive a DHCP offer (i.e. if you need to use DHCP to acquire an IP address that will work) it only blocks the ability for the virtual machine to act as a DHCP server.
QUESTION 365
You have a server named Server1 that runs Windows Server 2012 R2.
You plan to enable Hyper-V Network Virtualization on Server1.
You need to install the Windows Network Virtualization Filter Driver on Server1.
Which Windows PowerShell cmdlet should you run?
A. Set-NetVirtualizationGlobal
B. Enable-NetAdapterBinding
C. Add – WindowsFeature
D. Set-NetAdapterVmq
Answer: B
Explanation:
Hyper-V Network Virtrtualization runs multiple virtual networks on a physical network. And each virtual network operates as if it is running as a physical network. The The Set-NetAdaptercmdlet sets the basic properties of a network adapter such as virtual LAN (VLAN) identifier (ID) and MAC address. Thus if you add the binding parameter to the command then you will be able to install the Windows Network Virtualization Filter Driver.
Step one:Enable Windows Network Virtualization (WNV). This is a binding that is applied to the NIC that you External Virtual Switch is bound to. This can be a physical NIC, it can be an LBFO NIC team. Either way, it is the network adapter that your External Virtual Switch uses to exit the server.This also means that if you have multiple virtual networks or multiple interfaces that you can pick and choose and it is not some global setting.If you have one External Virtual Switch this is fairly easy:
$vSwitch = Get-VMSwitch -SwitchType External# Check if Network Virtualization is bound# This could be done by checking for the binding and seeing if it is enabledForEach-Object – InputObject $vSwitch {if ((Get-NetAdapterBinding -ComponentID “ms_netwnv” – InterfaceDescription $_.NetAdapterInterfaceDescription).Enabled -eq $false){ # Lets enable itEnable-NetAdapterBinding -InterfaceDescription $_.NetAdapterInterfaceDescription – ComponentID “ms_netwnv”}}
QUESTION 366
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed.
You have fixed-size VHD named Files.vhd.
You need to make the contents in Files.vhd available to several virtual machines.
The solution must meet the following requirements:
– Ensure that if the contents are changed on any virtual machine, the changes are not reflected on the other virtual machines.
– Minimize the amount of disk space used.
What should you do?
A. Create differencing VHD5 that use Files.vhd as the parent disk.
B. Create a fixed-size VHDX. Transfer the information from Files.vhd to the new VHDX file.
C. Convert Files.vhd to a dynamically expanding VHD.
D. Create a dynamically expanding VHDX. Transfer the information from Files.vhd to the new VHDX file.
Answer: A
QUESTION 367
Your network contains an Active Directory domain named contoso.com.
The domain contains Server 2012 R2 and has the Hyper-V server role installed.
You need to log the amount of system resources used by each virtual machine.
What should you do?
A. From Windows PowerShell, run the Enable-VMResourceMeteringcmdlet.
B. From Windows System Resource Manager, enable Accounting.
C. From Windows System Resource Manager, add a resource allocation policy.
D. From Windows PowerShell, run the Measure-VM cmdlet.
Answer: A
Explanation:
The Enable-VMResourceMeteringcmdlet collects resource utilization data for a virtual machine or resource pool.
QUESTION 368
Your network contains an Active Directory domain named contoso.com.
All domain controllers run Windows Server 2012 R2.
Administrators use client computers that run Windows 8 to perform all management tasks.
A central store is configured on a domain controller named DC1.
You have a custom administrative template file named AppLadmx. App1.admx contains application settings for an application named App1.
From a client computer named Computer1, you create a new Group Policy object (GPO) named GPO1.
You discover that the application settings for App1 fail to appear in GPO1.
You need to ensure that the App1 settings appear in all of the new GPOs that you create.
What should you do?
A. From the Default Domain Controllers Policy, add App1.admx to the Administrative Templates.
B. Copy App1.admx to \\Contoso.com\SYSVOL\Contoso.com\Policies\PolicyDefinitions\.
C. From the Default Domain Policy, add App1.admx to the Administrative Templates.
D. Copy App1.admx to \\Contoso.com\SYSVOL\Contoso.com\StarterGPOs.
Answer: B
Explanation:
To take advantage of the benefits of .admx files, you must create a Central Store in the SYSVOL folder on a domain controller. The Central Store is a file location that is checked by the Group Policy tools. The Group Policy tools use any .admx files that are in the Central Store. The files that are in the Central Store are later replicated to all domain controllers in the domain.
QUESTION 369
Your company has a main office and a branch office.
The network contains an Active Directory domain named contoso.com.
The main office contains a domain controller named DC1 that runs Windows Server 2012 R2.
DC1 is a DNS server and hosts a primary zone for contoso.com. The branch office contains a member server named Server1 that runs Windows Server 2012 R2. Server1 is a DNS server and hosts a secondary zone for contoso.com.
The main office connects to the branch office by using an unreliable WAN link.
You need to ensure that Server1 can resolve names in contoso.com if the WAN link in unavailable for three days.
Which setting should you modify in the start of authority (SOA) record?
A. Retry interval
B. Refresh interval
C. Expires after
D. Minimum (default) TTL
Answer: C
Explanation:
Used by other DNS servers that are configured to load and host the zone to determine when zone data expires if it is not renewed
QUESTION 370
Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains servers named Server1 and Server2 that run Windows Server 2012 R2.
You create a windows PowerShell script named Scriptl.psl that contains the following configuration: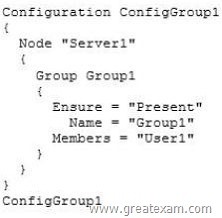
You need to apply the configuration to Server1.
The solution must ensure that the configuration on Server1 can be updated by modifying a MOF file on Server2.
Which actions should you perform on each server?
To answer, select the appropriate server on which to perform each action in the answer area.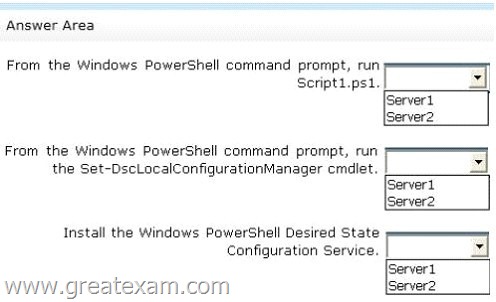
Answer: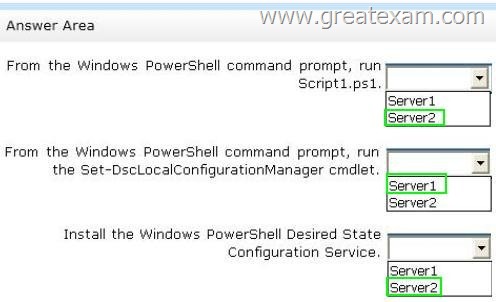
QUESTION 371
Hotspot Question
Your network contains an Active Directory domain named contoso.com.
The domain contains 25 servers. All servers run Windows Server 2012 R2.
You need to create a Windows Firewall rule to prevent administrators from using Internet Explorer to access the Internet while they are logged on interactively to the servers.
The solution must not prevent administrators from accessing websites on the internal network.
How should you configure the rule? To answer, select the appropriate options in the answer area.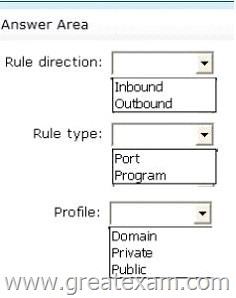
Answer: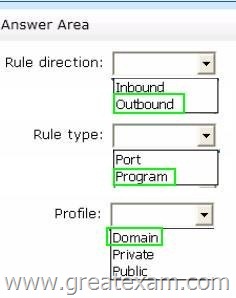
QUESTION 372
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1 that runs Windows Server 2012 R2.
Server1 contains a virtual machine named VM1 that runs Windows Server 2012 R2.
You need to ensure that a user named User1 can install Windows features on VM1.
The solution must minimize the number of permissions assigned to User1.
To which group should you add User1?
A. Server Operators on Server1
B. Power Users on VM1
C. Administrators on VM1
D. Hyper-V Administrators on Server1
Answer: D
Explanation:
* The Hyper-V role enables you to create and manage a virtualized computing environment by using virtualization technology that is built in to Windows Server 2012. Hyper-V virtualizes hardware to provide an environment in which you can run multiple operating systems at the same time on one physical computer, by running each operating system in its own virtual machine.
* Simplified authorization
The Hyper-V Administrators group is introduced in Windows Server 2012 and is implemented as a local security group.
What value does this change add?
This group can reduce the number of users that belong to the local Administrators group while providing users with access to Hyper-V.
What works differently?
The Hyper-V Administrators group is a new local security group. Add users to this group instead of the local Administrators group to provide them with access to Hyper-V. Members of the Hyper-V Administrators have complete and unrestricted access to all features of Hyper-V.
Reference: What’s New in Hyper-V for Windows Server 2012
QUESTION 373
Your network contains two DNS servers named DNS1 and DNS2 that run Windows Server 2012 R2. DNS1 has a primary zone named contoso.com.
DNS2 has a secondary copy of the contoso.com zone.
You need to log the zone transfer packets sent between DNS1 and DNS2.
What should you configure?
A. debug logging from DNS Manager
B. logging from Windows Firewall with Advanced Security
C. monitoring from DNS Manager
D. a Data Collector Set (DCS) from Performance Monitor
Answer: C
Explanation:
Monitoring DNS with the DNS Console
The DNS management console includes functionality that enables you to use the console to monitor DNS activity:
* Event Logging tab: You can access the Event Logging tab located within the Properties dialog box of the DNS server to specify the DNS events that you want to monitor. Through the Event Logging tab, you can limit the events which are written to the DNS Events log.
* Monitoring tab: The Monitoring tab is also located within the Properties dialog box of the DNS server. This tab allows you to test querying of the DNS server.
QUESTION 374
Your network contains an Active Directory domain named contoso.com.
All servers run Windows Server 2012 R2.
Client computers run either Windows 7 or Windows 8.
All of the client computers have an application named App1 installed.
The domain contains a Group Policy object (GPO) named GPO1 that is applied to all of the client computers.
You need to add a system variable named App1Data to all of the client computers.
Which Group Policy preference should you configure?
A. Ini Files
B. Data Sources
C. Services
D. Environment
Answer: D
Explanation:
Environment Variable preference items allow you to create, update, replace, and delete user and system environment variables or semicolon-delimited segments of the PATH variable.
Note:
Creating an Environment Variable item
To create a new Environment Variable preference item
1. Open the Group Policy Management Console . Right-click the Group Policy object (GPO) that should contain the new preference item, and then click Edit .
2. In the console tree under Computer Configuration or User Configuration , expand the Preferences folder, and then expand the Windows Settings folder.
3. Right-click the Environment node, point to New , and select Environment Variable .
4. In the New Environment Variable Properties dialog box, select an Action for Group Policy to perform. (For more information, see “Actions” in this topic.)
5. Enter environment variable settings for Group Policy to configure or remove.
6. Click the Common tab, configure any options, and then type your comments in the Description box.
7. Click OK . The new preference item appears in the details pane.
QUESTION 375
Your network contains an Active Directory domain named contoso.com.
The domain contains six domain controllers named DO, DC2, DC3, DC4, DC5 and DC6.
Each domain controller has the DNS Server server role installed and hosts an Active Directory-integrated zone for contoso.com.
You plan to create a new Active Directory-integrated zone named litwareinc.com that will be used for testing.
You need to ensure that the new zone will be available only on DC5 and DC6.
What should you do first?
A. Create an Active Directory connection object.
B. Create an Active Directory site link.
C. Create an application directory partition
D. Change the zone replication scope.
Answer: C
Explanation:
Zone replication scope: All domain controllers in a specified application directory partition Replicates zone data according to the replication scope of the specified application directory partition. For a zone to be stored in the specified application directory partition, the DNS server hosting the zone must be enlisted in the specified application directory partition. Use this scope when you want zone data to be replicated to domain controllers in multiple domains but you do not want the data to replicate to the entire forest.
QUESTION 376
Your network contains a server named Server1 that has the Network Policy and Access Services server role installed.
AH of the network access servers forward connection requests to Server1.
You create a new network policy on Server1.
You need to ensure that the new policy applies only to connection requests from the 192.168.0.0/24 subnet.
What should you do?
A. Set the Client IP4 Address condition to 192.168.0.0/24.
B. Set the Client IP4 Address condition to 192.168.0.
C. Set the Called Station ID constraint to 192.168.0_0/24.
D. Set the Called Station ID constraint to 192_168.0
Answer: A
Explanation:
After creating a network policy with the New Network Policy Wizard or by creating a custom policy, you can specify the conditions that connection requests must have in order to match the network policy; if the conditions configured in the policy match the connection request, Network Policy Server (NPS) applies the settings designated in the network policy to the connection.
Incorrect:
Not C, not D: Called station ID
Allows you to specify the telephone number of the dial-up server that clients are allowed to use to access the network.
QUESTION 377
Your network contains an Active Directory domain named contoso.com. The domain contains six domain controllers. The domain controllers are configured as shown in the following table.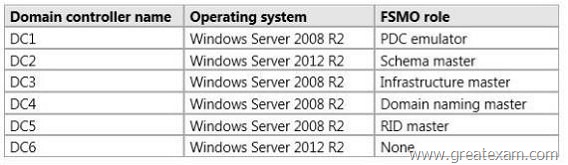
The network contains a server named Server1 that has the Hyper-V server role installed.
DC6 is a virtual machine that is hosted on Server1.
You need to ensure that you can clone DC6.
What should you do?
A. Transfer the PDC emulator to DC5
B. Transfer the schema master to DC4
C. Transfer the PDC emulator to DC2
D. Transfer the schema master to DC6
Answer: C
Explanation:
A Windows Server 2012 Server running the PDC emulator is required.
The requirements for virtualized DC cloning include:
* The PDC emulator must run Windows Server 2012. You can clone PDC emulator if it is virtualized.
* The virtualized DC that is used as a source for cloning must run Windows Server 2012 and be a member of the Cloneable Domain Controllers group.
Note: Using virtualized domain controller cloning in Windows Server 2012 to expedite forest recovery Virtualized domain controller (DC) cloning simplifies and expedites the process for installing additional virtualized DCs in a domain, especially in centralized locations such as datacenters where several DCs run on hypervisors. After you restore one virtual DC in each domain from backup, additional DCs in each domain can be rapidly brought online by using the virtualized DC cloning process. You can prepare the first virtualized DC that you recover, shut it down, and then copy that virtual hard disk as many times as is necessary in order to create cloned virtualized DCs to build out the domain.
QUESTION 378
Your company deploys a new Active Directory forest named contoso.com.
The first domain controller in the forest runs Windows Server 2012 R2.
The forest contains a domain controller named DC10.
On DC10, the disk that contains the SYSVOL folder fails.
You replace the failed disk. You stop the Distributed File System (DFS) Replication service.
You restore the SYSVOL folder.
You need to perform a non-authoritative synchronization of SYSVOL on DC10.
Which tool should you use before you start the DFS Replication service on DC10?
A. Dfsgui.msc
B. Ultrasound
C. Ldp
D. Replmon
Answer: C
Explanation:
You need to change the msDFSR-Enabled value before syncing, so you would need to use ADSIEDIT or another tool such as Ldp.
QUESTION 379
Hotspot Question
You have a server named LON-SRV1 that runs Windows Server 2012 R2. LON-SVR1 has the Remote server role installed. LON-SVR1 is located in the perimeter network.
The IPv4 routing table on LON-SVR1 is configured as shown in the following exhibit. (Click the Exhibit Button)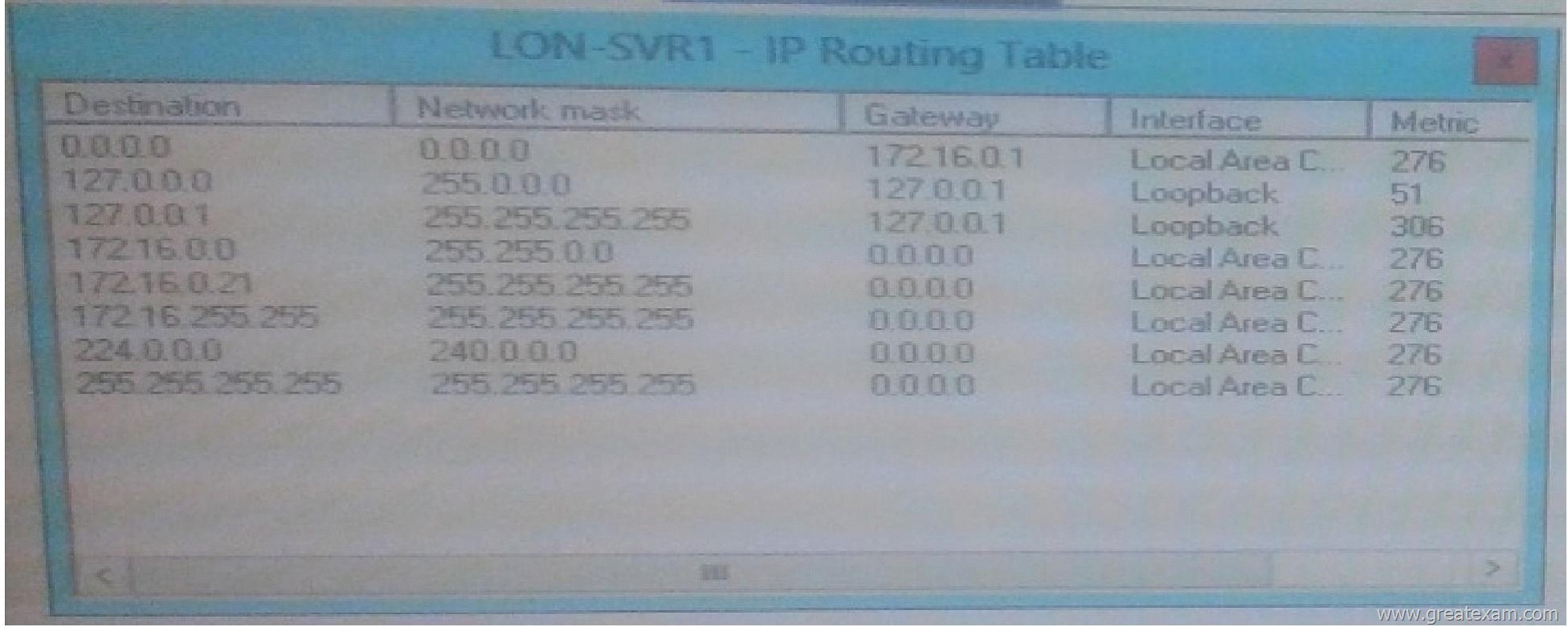
Your company purchases an additional router named router named Router1.
Router1 has an interface that connects to perimeter network and an interface that connects to the Internet. The IP address of interface that connects to the perimeter network is 172.16.0.2.
You need to ensure that LON-SRV1 will route traffic to the internet by using Router1 if the current detail gateway is unavailable.
How should you configure the static route on LON-SRV1?
To answer, select the appropriate static route in the answer area.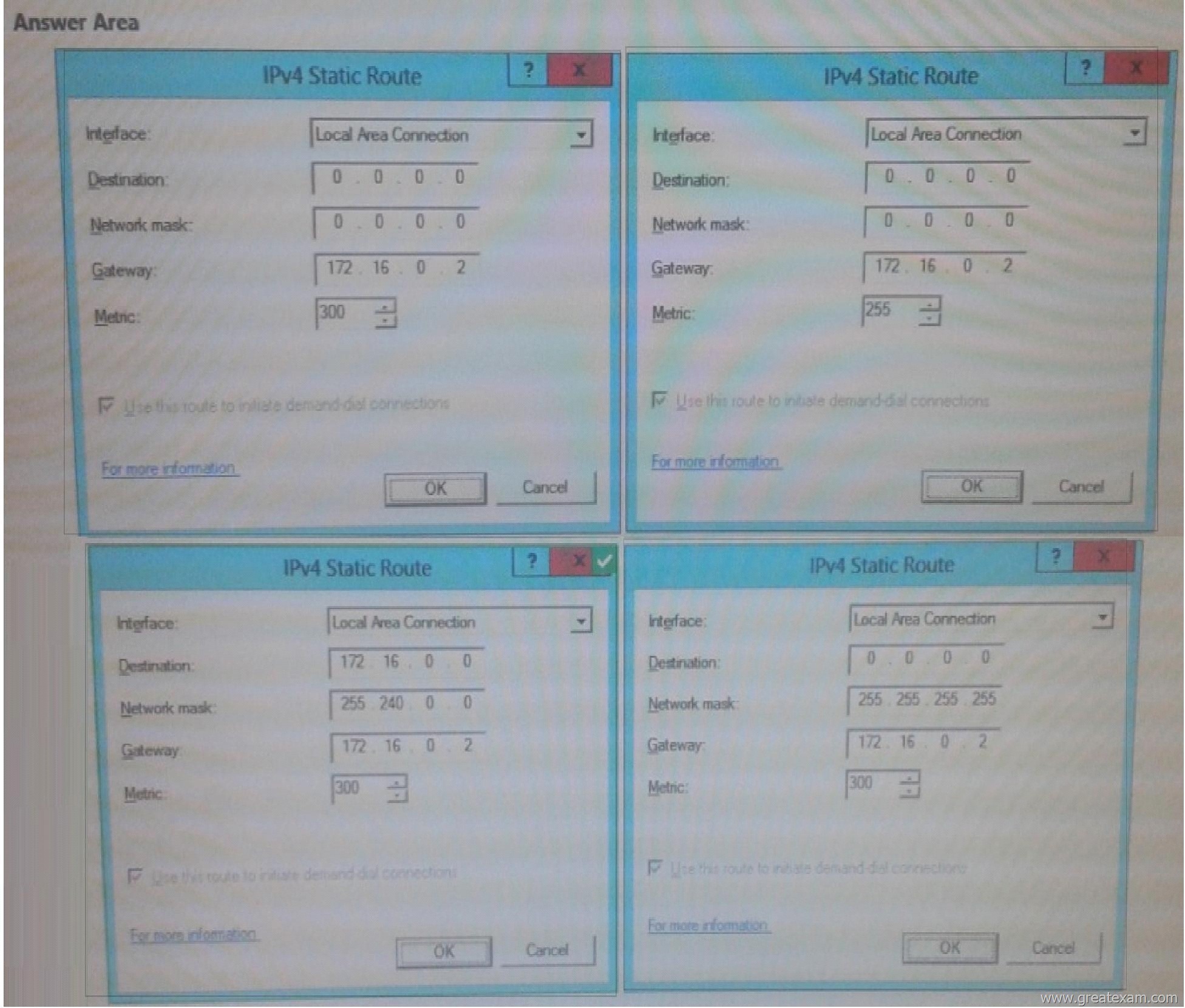
Answer: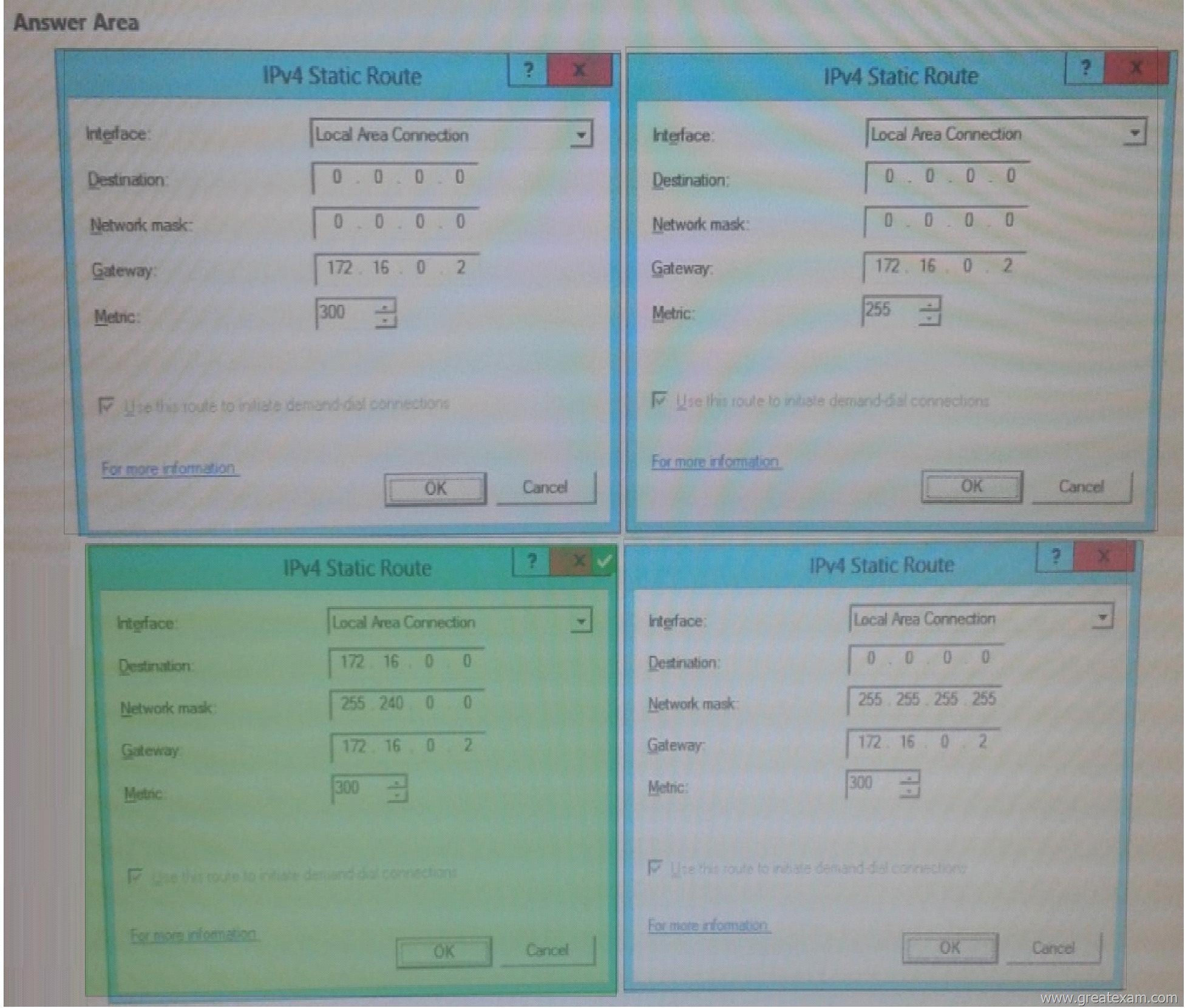
QUESTION 380
You have a small Hyper-V cluster built on two hosts that run Windows Server 2012 R2 Hyper-V. You manage the virtual infrastructure by using System Center Virtual Machine Manager 2012.
Distributed Key Management is not installed.
You have the following servers in the environment: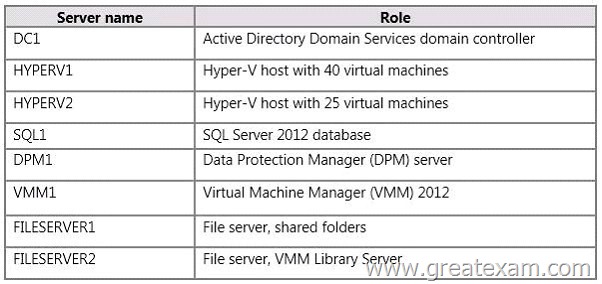
You have the following requirements:
– You must back up virtual machines at the host level.
– You must be able to back up virtual machines that are configured for live migration.
– You must be able to restore the entire VMM infrastructure.
You need to design and implement the backup plan.
What should you do?
A. Run the following Windows PowerShell command:
Checkpoint-VM -Name DPMI -ComputerName SQL1
B. Install the DPM console on VMM1
C. Configure backup for all disk volumes on FILESERVER1.
D. Install the VMM console on DPMI.
Answer: A
Get latest GreatExam 70-417 practice test and pass your exam easily. Passing the test is not so difficult now, you can easily pass the exam with our correct and accurate collection of GreatExam 70-417 question answers.
http://www.greatexam.com/70-417-exam-questions.html