If you are not prepared for Microsoft 70-417 exam, please don’t worry. You can pass Microsoft 70-417 exam very simply and easily with our free 70-417 dumps. With our braindumps you shall get GreatExam 70-417 PDF & VCE. After preparing from our free Microsoft 70-417 GreatExam practice test you shall not only pass this exam as well you will get good marks in very short time.
QUESTION 41
Your network contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed. Server1 hosts four virtual machines named VM1, VM2, VM3, and VM4. Server1 is configured as shown in the following table.
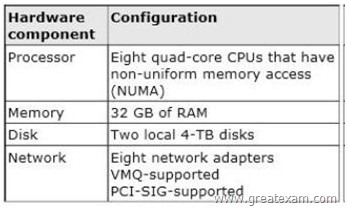
You install a network monitoring Application on VM2.
You need to ensure that all of the traffic sent to VM3 can be captured on VM2.
What should you configure?
A. NUMA topology
B. Resource control
C. Resource metering
D. Virtual Machine Chimney
E. The VLAN ID
F. Processor Compatibility
G. The startup order
H. Automatic Start Action
I. Integration Services
J. Port mirroring
K. Single-root I/O virtualization
Answer: J
Explanation:
With Hyper-V Virtual Switch port mirroring, you can select the switch ports that are monitored as well as the switch port that receives copies of all the traffic. And since Port mirroring allows the network traffic of a virtual machine to be monitored by copying the traffic and forwarding it to another virtual machine that is configured for monitoring, you should configure port mirroring on VM2.
http://technet.microsoft.com/en-us/library/jj679878.aspx#bkmk_portmirror
QUESTION 42
Your network contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed. Server1 hosts four virtual machines named VM1, VM2, VM3, and VM4. Server1 is configured as shown in the following table.
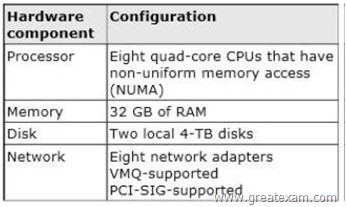
You need to configure VM4 to track the CPU, memory, and network usage.
What should you configure?
A. NUMA topology
B. Resource control
C. Resource metering
D. Virtual Machine Chimney
E. The VLAN ID
F. Processor Compatibility
G. The startup order
H. Automatic Start Action
I. Integration Services
J. Port mirroring
K. Single-root I/O virtualization
Answer: C
Explanation:
http://blogs.technet.com/b/meamcs/archive/2012/05/28/hyper-v-resource-metering-in-windows-server-2012-server-8-beta.aspx
Hyper-V Resource Metering in Windows Server 2012 R2 “Server 8 Beta”
IT organizations need tools to charge back business units that they support while providing the business units with the right amount of resources to match their needs. For hosting providers, it is equally important to issue chargebacks based on the amount of usage by each customer.
To implement advanced billing strategies that measure both the assigned capacity of a resource and its actual usage, earlier versions of Hyper-V required users to develop their own chargeback solutions that polled and aggregated performance counters.
These solutions could be expensive to develop and sometimes led to loss of historical data.
To assist with more accurate, streamlined chargebacks while protecting historical information, Hyper-V in Windows Server 2012 R2 “Server 8 Beta” introduces Resource Metering, a feature that allows customers to create cost-effective, usage-based billing solutions. With this feature, service providers can choose the best billing strategy for their business model, and independent software vendors can develop more reliable, end-to-end chargeback solutions on top of Hyper-V.
Metrics collected for each virtual machine
§ Average CPU usage, measured in megahertz over a period of time.
§ Average physical memory usage, measured in megabytes.
§ Minimum memory usage (lowest amount of physical memory).
§ Maximum memory usage (highest amount of physical memory).
§ Maximum amount of disk space allocated to a virtual machine.
§ Total incoming network traffic, measured in megabytes, for a virtual network adapter.
§ Total outgoing network traffic, measured in megabytes, for a virtual network adapter
To enable Hyper-V resource metering on hyper-v host HV01 run the following PowerShell commands:
Get-VM -ComputerName HV01 | Enable-VMResourceMetering
By default the collection interval for Hyper-v metering data is one hour to change this interval the following PowerShell command can be used “value used in the command below is one minute”:
Set-vmhost – computername HV01 – ResourceMeteringSaveInterval 00:01:00
To get all VMs metering data run the following PowerShell command:
Get-VM -ComputerName HV01 | Measure-VM
To get a particular VM “test01” metering data run the following PowerShell command:
Get-VM -ComputerName HV01 -Name “test01” | Measure-VM
QUESTION 43
You are a network administrator of an Active Directory domain named contoso.com.
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the DHCP Server server role and the Network Policy Server role service installed.
You enable Network Access Protection (NAP) on all of the DHCP scopes on Server1.
You need to create a DHCP policy that willApply to all of the NAP non-compliant DHCP clients. Which criteria should you specify when you create the DHCP policy?
A. The relay agent information
B. The client identifier
C. The vendor class
D. The user class
Answer: D
QUESTION 44
Drag and Drop Question
Your network contains an Active Directory domain named adatum.com.
The domain contains a server named Server1 that runs Windows Server 2012 R2.
Server1 is configured as a Network Policy Server (NPS) server and as a DHCP server.
You need to log all DHCP clients that have Windows Firewall disabled.
Which three actions should you perform in sequence? To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the correct order.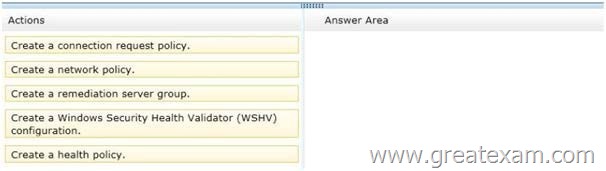
Answer: 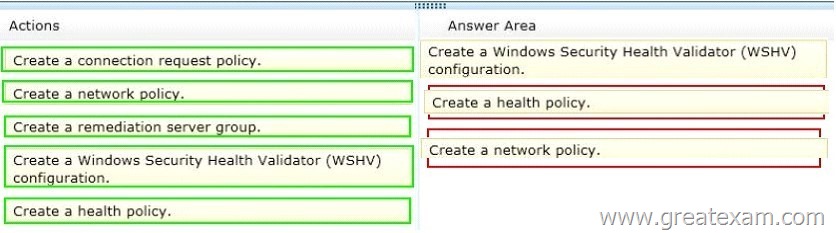
QUESTION 45
Your network contains an Active Directory domain named contoso.com.
The domain contains a domain controller named DC1 that runs Windows Server 2012 R2.
You mount an Active Directory snapshot on DC1.
You need to expose the snapshot as an LDAP server.
Which tool should you use?
A. Ldp
B. Ntdsutil
C. ADSI Edit
D. Dsamain
Answer: D
Explanation:
Dsamain.exe can you can use to expose the snapshot data as an LDAP server
QUESTION 46
Your network contains an Active Directory forest named contoso.com.
The forest contains a single domain. All domain controllers run Windows Server 2012 R2.
The domain contains two domain controllers.
The domain controllers are configured as shown in the following table.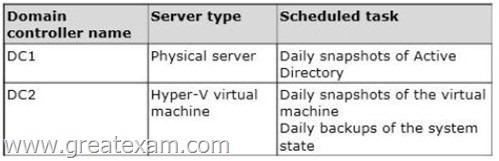
Active Directory Recycle Bin is enabled.
You discover that a support technician accidentally removed 100 users from an Active Directory group named Group1 an hour ago.
You need to restore the membership of Group1.
What should you do?
A. Perform an authoritative restore.
B. Perform a non-authoritative restore.
C. Recover the items by using Active Directory Recycle Bin.
D. Apply a virtual machine snapshot to VM1.
Answer: A
Explanation:
Authoritative restore allows the administrator to recover a domain controller, restore it to a specific point in time, and mark objects in Active Directory as being authoritative with respect to their replication partners. For example, you might need to perform an authoritative restore if an administrator inadvertently deletes an organizational unit containing a large number of users. If you restore the server from tape, the normal replication process would not restore the inadvertently deleted organizational unit. Authoritative restore allows you to mark the organizational unit as authoritative and force the replication process to restore it to all of the other domain controllers in the domain.
Incorrect:
Not C: A nonauthoritative restore returns the domain controller to its state at the time of backup and then allows normal replication to overwrite that state with any changes that occurred after the backup was taken. After you restore the system state, the domain controller queries its replication partners. The replication partners replicate any changes to the restored domain controller, ensuring that the domain controller has an accurate and updated copy of the Active Directory database.
QUESTION 47
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2. In a remote site, a support technician installs a server named DC10 that runs Windows Server 2012 R2. DC10 is currently a member of a workgroup.
You plan to promote DC10 to a read-only domain controller (RODC).
You need to ensure that a user named Contoso\User1 can promote DC10 to a RODC in the contoso.com domain.
The solution must minimize the number of permissions assigned to User1. What should you do?
A. From Active Directory Administrative Center, pre-create an RODC computer account.
B. FromNtdsutil, run the local roles command.
C. FromDsmgmt, run the local roles command.
D. Join DC10 to the domain. Run dsmod and specify the /server switch.
Answer: A
Explanation:
A staged read only domain controller (RODC) installation works in two discrete phases:
1. Staging an unoccupied computer account
2. Attaching an RODC to that account during promotion
Reference: Install a Windows Server 2012 R2 Active Directory Read-Only Domain Controller (RODC)
QUESTION 48
Your network contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed. Server1 hosts four virtual machines named VM1, VM2, VM3, and VM4. Server1 is configured as shown in the following table.
VM2 sends and receives large amounts of data over the network.
You need to ensure that the network traffic of VM2 bypasses the virtual switches of the parent partition.
What should you configure?
A. NUMA topology
B. Resource control
C. Resource metering
D. Virtual Machine Chimney
E. The VLAN ID
F. Processor Compatibility
G. The startup order
H. Automatic Start Action
I. Integration Services
J. Port mirroring
K. Single-root I/O virtualization
Answer: K
Explanation:
http://technet.microsoft.com/en-us/library/hh831410.aspx
Single-root I/O virtualization -capable network adapters can be assigned directly to a virtual machine to maximize network throughput while minimizing network latency and the CPU overhead required for processing network traffic.
QUESTION 49
Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server2. Server1 runs Windows Server 2012 R2. Server2 runs Windows Server 2008 R2 Service Pack 1 (SP1) and has the DHCP Server server role installed.
You need to manage DHCP on Server2 by using the DHCP console on Server1.
What should you do first?
A. From the Microsoft Management Console on Server1, add a snap-in.
B. From Server Manager on Server2, enable Windows Remote Management.
C. From Windows PowerShell on Server2, run Enable-PSRemoting.
D. From Server Manager on Server1, install a feature.
Answer: D
Explanation:
When the DHCP role is installed, it appears that the firewall rules are automatically added. This means you only need to add the DHCP Manager MMC snap-in which is a Role Administration Tool feature.
QUESTION 50
Your network contains an Active Directory domain named contoso.com.
The domain contains a domain controller named dcl.contoso.com.
You discover that the Default Domain Policy Group Policy objects (GPOs) and the Default Domain Controllers Policy GPOs were deleted.
You need to recover the Default Domain Policy and the Default Domain Controllers Policy GPOs.
What should you run?
A. dcgpofix.exe /target:domain
B. dcgpofix.exe /target:both
C. gpfixup.exe /oldnb:contoso/newnb:dc1
D. gpfixup.exe /dc:dc1.contoso.com
Answer: B
Explanation:
http://technet.microsoft.com/en-us/library/cc739095(v=ws.10).aspx
QUESTION 51
Hotspot Question
You have a server named Server1 that runs Windows Server 2012 R2.
The volumes on Server1 are configured as shown in the following table.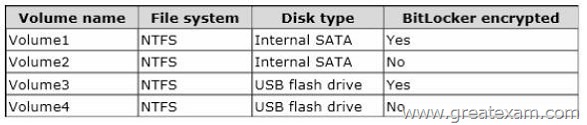
A new corporate policy states that backups must use Windows Azure Backup whenever possible.
You need to identify which backup methods you must use to back up Server1.
The solution must use Windows Azure Backup whenever possible.
Which backup type should you identify for each volume? To answer, select the appropriate backup type for each volume in the answer area.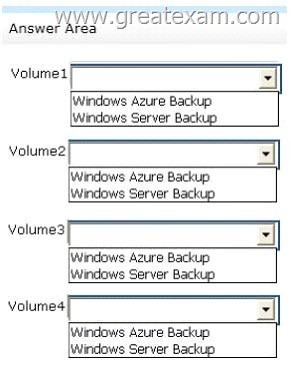
Answer: 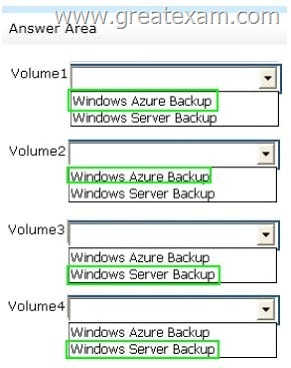
QUESTION 52
Your network contains an Active Directory domain named contoso.com.
All domain controllers run Windows Server 2012 R2.
An organizational unit (OU) named OU1 contains 200 client computers that run Windows 8 Enterprise. A Group Policy object (GPO) named GPO1 is linked to OU1.
You make a change to GPO1.
You need to force all of the computers in OU1 to refresh their Group Policy settings immediately. The solution must minimize administrative effort.
Which tool should you use?
A. The Secedit command
B. The Invoke-GpUpdatecmdlet
C. Group Policy Object Editor
D. Server Manager
Answer: B
Explanation:
https://technet.microsoft.com/en-us/library/jj134201.aspx
QUESTION 53
Your network contains an Active Directory domain named contoso.com.
The domain contains a member server named Server1 that has the Active Directory Federation Services server role installed. All servers run Windows Server 2012.
You complete the Active Directory Federation Services Configuration Wizard on Server1.
You need to ensure that client devices on the internal network can use Workplace Join.
Which two actions should you perform on Server1? (Each correct answer presents part of the solution. Choose two.)
A. Run Enable AdfsDeviceRegistration -PrepareActiveDirectory.
B. Edit the multi-factor authentication global authentication policy settings.
C. Edit the primary authentication global authentication policy settings.
D. Run Set-AdfsProxyPropertiesHttpPort 80.
E. Run Enable-AdfsDeviceRegistration.
Answer: CE
Explanation/:
* To enable Device Registration Service
On your federation server, open a Windows PowerShell command window and type:
Enable-AdfsDeviceRegistration
Repeat this step on each federation farm node in your AD FS farm..
Enable seamless second factor authentication
Seamless second factor authentication is an enhancement in AD FS that provides an added level of access protection to corporate resources and applications from external devices that are trying to access them. When a personal device is Workplace Joined, it becomes a `known’ device and administrators can use this information to drive conditional access and gate access to resources.
To enable seamless second factor authentication, persistent single sign-on (SSO) and conditional access for Workplace Joined devices
In the AD FS Management console, navigate to Authentication Policies.
Select Edit Global Primary Authentication.
Select the check box next to Enable Device Authentication, and then click OK.
QUESTION 54
Your company deploys a new Active Directory forest named contoso.com. The first domain controller in the forest runs Windows Server 2012 R2. The forest contains a domain controller named DC10.
On DC10, the disk that contains the SYSVOL folder fails.
You replace the failed disk.
You stop the Distributed File System (DFS) Replication service.
You restore the SYSVOL folder.
You need to perform a non-authoritative synchronization of SYSVOL on DC10.
Which tool should you use before you start the DFS Replication service on DC10?
A. Active Directory Sites and Services
B. Ultrasound
C. Adsiedit.msc
D. Frsutil
Answer: C
Explanation:
How to perform a non-authoritative synchronization of DFSR-replicated SYSVOL
(like “D2” for FRS)
1. In the ADSIEDIT.MSC tool modify the following distinguished name (DN) value and attribute on each of the domain controllers that you want to make non- authoritative:CN=SYSVOL Subscription,CN=Domain System Volume,CN=DFSR- LocalSettings,CN=<the server name>,OU=Domain Controllers,DC=<domain>msDFSR- Enabled=FALSE
2. Force Active Directory replication throughout the domain.
Etc
QUESTION 55
Drag and Drop Question
Your network contains an Active Directory domain named contoso.com.
You need to ensure that third-party devices can use Workplace Join to access domain resources on the Internet.
Which four actions should you perform in sequence? To answer, move the appropriate four actions from the list of actions to the answer area and arrange them in the correct order.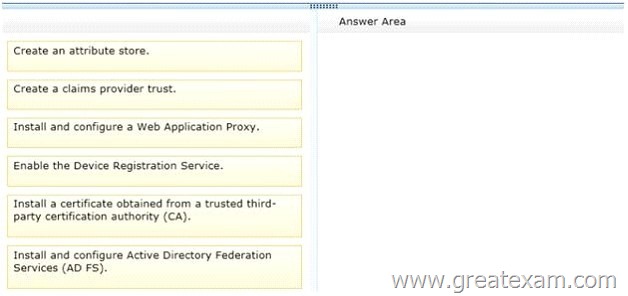
Answer: 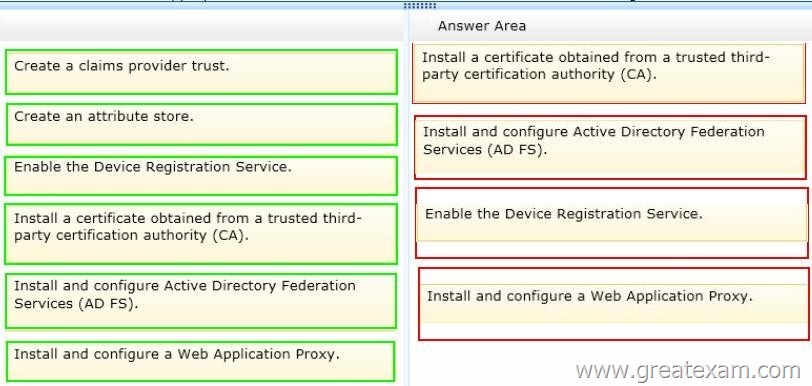
QUESTION 56
Your network contains two servers named HV1 and HV2.
Both servers run Windows Server 2012 R2 and have the Hyper-V server role installed.
HV1 hosts 25 virtual machines. The virtual machine configuration files and the virtual hard disks are stored in D:\VM.
You shut down all of the virtual machines on HV1.
You copy D:\VM to D:\VM on HV2.
You need to start all of the virtual machines on HV2.
You want to achieve this goal by using the minimum amount of administrative effort.
What should you do?
A. From HV1, export all virtual machines to D:\VM.
Copy D:\VM to D:\VM on HV2 and overwrite the existing files.
On HV2, run the New Virtual Machine wizard.
B. From HV1, export all virtual machines to D:\VM.
Copy D:\VM to D:\VM on HV2 and overwrite the existing files.
On HV2, run the Import Virtual Machine wizard.
C. Run the Import-VM InitialReplicationcmdlet.
D. Run the Import-VM cmdlet.
Answer: D
Explanation:
The Import-VM cmdlet imports a virtual machine from a file.
QUESTION 57
Hotspot Question
Your network contains an Active Directory domain named contoso.com.
The domain contains a domain controller named DC1 and a member server named Server1.
All servers run Windows Server 2012 R2.
You install the IP Address Management (IPAM) Server feature on Server1.
From the Provision IPAM wizard, you select the Group Policy Based provisioning method and enter a GPO name prefix of IPAM1.
You need to provision IPAM by using Group Policy.
What command should you run on Server1 to complete the process? To answer, select the appropriate options in the answer area.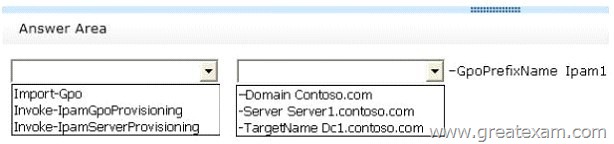
Answer: 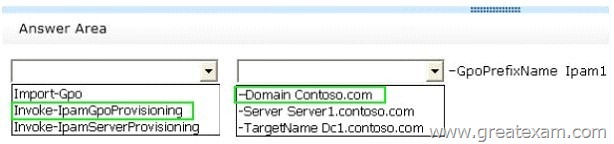
QUESTION 58
Hotspot Question
Your network contains an Active Directory domain named fabrikam.com.
You implement DirectAccess.
You need to view the properties of the DirectAccess connection.
Which connection properties should you view?
To answer, select the appropriate connection properties in the answer area.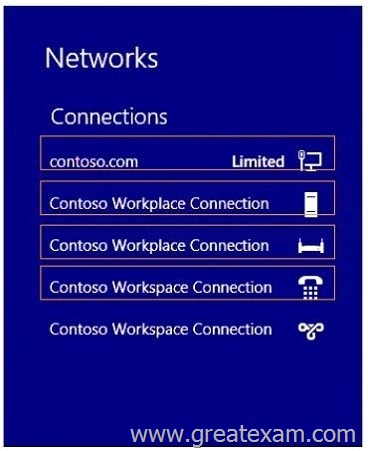
Answer: 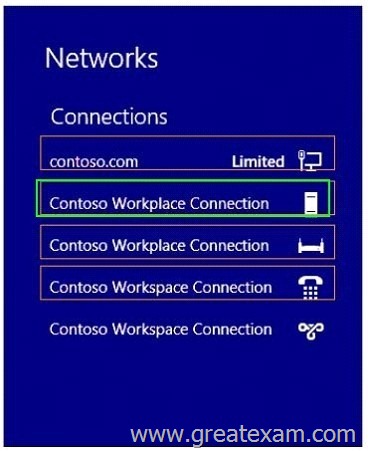
QUESTION 59
Your network contains an Active Directory domain named contoso.com. The domain contains servers named Server1 and Server2 that run Windows Server 2012 R2. Server1 has the Active Directory Federation Services server role installed.Server2 is a file server.
Your company introduces a Bring Your Own Device (BYOD) policy.
You need to ensure that users can use a personal device to access domain resources by using Single Sign-On (SSO) while they are connected to the internal network.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Enable the Device Registration Service in Active Directory.
B. Publish the Device Registration Service by using a Web Application Proxy.
C. Configure Active Directory Federation Services (AD FS) for the Device Registration Service.
D. Install the Work Folders role service on Server2.
E. Create and configure a sync share on Server2.
Answer: AC
Explanation:
*Prepare your Active Directory forest to support devices
This is a one-time operation that you must run to prepare your Active Directory forest to support devices.
To prepare the Active Directory forest
On your federation server, open a Windows PowerShell command window and type:
Initialize-ADDeviceRegistration
*Enable Device Registration Service on a federation server farm node To enable Device Registration Service
1.On your federation server, open a Windows PowerShell command window and type:
Enable-AdfsDeviceRegistration
2.Repeat this step on each federation farm node in your AD FS farm.
QUESTION 60
Hotspot Question
Your network contains an Active Directory domain named contoso.com.
You install the IP Address Management (IPAM) Server feature on a server named Server1 and select Manual as the provisioning method.
The IPAM database is located on a server named SQL1.
You need to configure IPAM to use Group Policy Based provisioning.
What command should you run first? To answer, select the appropriate options in the answer area.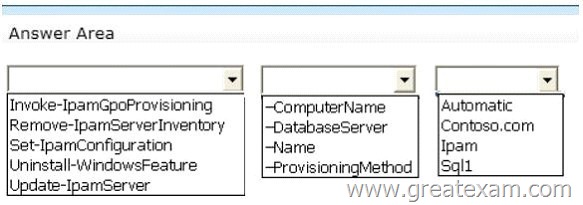
Answer: 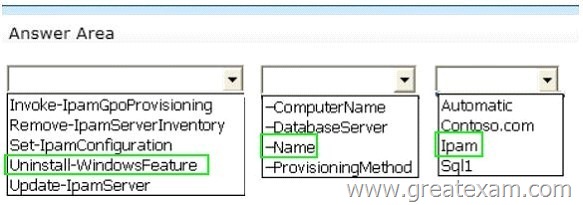
If you want to prepare for 70-417 exam in shortest time, with minimum effort but for most effective result, you can use GreatExam 70-417 practice test which simulates the actual testing environment and allows you to focus on various sections of 70-417 exam. Our candidates walk into the testing room as confident as a Certification Administrator. So you can pass the exam without any question.
http://www.greatexam.com/70-417-exam-questions.html