Are you worring about the 70-448 exam? GreatExam provides the latest 70-448 braindumps and guarantees you passing 70-448 exam beyond any doubt.
QUESTION 201
You manage the security in SQL Server 2008 R2 Reporting Services (SSRS).
You create a new role.
You need to grant the following permissions to the role:
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Assign Set Security Policies for Items task to the role.
B. Assign the Consume Reports task to the role,
C. Assign the Manage Resources task to the role.
D. Assign the Manage Reports task to the role.
Answer: AD
Explanation:
You can modify the My Reports role to suit your needs. However, it is recommended that you keep the “Manage reports” task and the “Manage folders” task to enable basic content management. In addition, this role should support all view-based tasks so that users can see folder contents and run the reports that they manage. Although the “Set security policies for items” task is not part of the role definition by default, you can add this task to the My Reports role so that users can customize security settings for subfolders and reports.
The Manage reports task:
Add and delete reports, modify report parameters, view and modify report properties, view and modify data sources that provide content to the report, view and modify report definitions, and set security policies at the report level.
Note:
Reporting Services uses a role-based security model to control access to reports, folders, and other items that are managed by a report server. The model maps a specific user or group to a role, and the role describes how that user or group is to access a given report or item. The security model consists of the following components:
A user or a group account that can be authenticated by Windows security or another authentication mechanism.
Role definitions that define a set of actions or operations. Examples of role definitions include System Administrator, Content Manager, and Publisher. Securable items for which you want to control access. Examples of securable items include folders, reports, and resources.
The combination of all these elements is characterized as a role assignment. In Reporting Services, role assignments provide the security context for items and the report server itself.
Note 2:
In Reporting Services, tasks are all possible actions that a user or administrator performs. There are twenty tasks in all. Some examples of tasks include “View reports,” “Manage reports,” and “Manage report server properties.”
Tasks are predefined. You cannot create custom tasks or modify the ones provided either programmatically or through a tool.
Each task consists of a set of permissions, which are also predefined. For example, the “Manage folders” task contains the permissions create and delete folders, and view and update folder properties. Users never interact with permissions directly. Users are granted permissions indirectly through the tasks that are included in role definitions. These permissions allow access to specific report server functionality. For example, users who have permission to subscribe to reports can use subscription-related pages and buttons in Report Manager to create and manage subscriptions. Users who do not have permission do not see subscription-related pages in Report Manager. To work, a task must be assigned to a role that is actively used in a security policy. A task that is not assigned to a role has no impact on user actions or security.
QUESTION 202
You are designing a SQL Server 2008 Integration Services (SSIS) package. The package will be used to extract data from a SQL Server 2008 database and load data to a Microsoft Office Excel workbook.
You need to ensure that the package creates a new worksheet in an existing Excel workbook during execution.
Which control flow component should you use to create the worksheet?
A. File System Task
B. Execute SQL Task
C. Data Flow Task along with the OLE DB source
D. Bulk Insert Task
Answer: C
Explanation:
Data flow tasks within SSIS can be used to move data from a source to destination and at the same time use certain transformation tasks to clean and modify the data while it is transferred. By adding a data flow task to the package control flow the package can be made to perform data extraction, transformation and load (ETL) operations.
A: File System Task is used to perform operations on files and folders, such as create, move, delete, and also to set the attributes for files and folders.
B: The Execute SQL Task can be used to execute any TSQL code
D: The Bulk Insert Task can be used to insert data from a text file or a flat file into a SQL Server Table
QUESTION 203
You maintain a SQL Server 2008 Analysis Services (SSAS) instance.
You plan to process the aggregations of a cube by using an XML for Analysts (XMLA) script.
You need to ensure that only the aggregations are updated.
What should you do?
A. Execute a processStructure command.
B. Execute a processUpdate command.
C. Execute a processIndex command.
D. Execute a processData command.
Answer: A
Explanation:
B: processUpdate only supported for dimensions
C: processIndex updates indexes and aggregations
D: processData processes data only without updating aggregations or indexes
QUESTION 204
You administer an instance of SQL Server Analysis Services (SSAS).
To troubleshoot access rights issues, you need to find out which roles are applied to a user.
Which event should you trace in Microsoft SQL Profiler?
A. The Audit Login event
B. The Audit Object Permissions event
C. The Session Initialize event
D. The Notification event
Answer: B
QUESTION 205
You are developing a SQL Server 2008 Reporting Services (SSRS) report.
The organization requires a drilldown report that color coordinates the values of students’ test scores. All average scores 70% or higher should have a green background.
All lower average scores should have a red background.
You need to enable this functionality.
Which expression should you use?
A. =iif(Fields!TestScore.Value >=.70, Green, Red)
B. =iif(Fields!TestScore.Value >=.70 THEN “Green” ELSE “Red”)
C. =iif(avg(FieldsSTestScore.Value)>=.70 THEN “Green” , “Red”)
D. =iif(avg(Fields!TestScore.Value)>=.70,”Green”,”Red”)
Answer: C
QUESTION 206
You create a SQL Server 2008 Reporting Services (SSRS) report for a school district.
The school district needs to be able to retrieve the median value of all test scores.
You build a custom function named Median that accepts the test scores and returns the median test score.
You need to run this custom function.
Which expression should you use?
A. =Execute Function Median(Fields!TestScores)
B. =Code.Function.Median()
C. =Code.Median(Fields!TestScores)
D. =Execute.Median(Fields!TestScores)
Answer: C
QUESTION 207
You have a SQL Server 2008 R2 Analysis Services (SSAS) solution.
You add a new Data Source View (DSV) to the solution.
The DSV includes a SalesOrder table with columns for OrderTotal and CostTotal.
You need to derive the profit for each order without modifying the underlying data.
What should you do?
A. Add a Named Calculation to the SalesOrder table, using OrderTotal + CostTotal as the expression.
B. Add a Named Calculation to the SalesOrder table, using OrderTotal, CostTotal as the expression.
C. Add a Named Query to the DSV, using Select * From SalesOrder as the expression.
D. Add a Named Calculation to the SalesOrder table, using OrderTotal – CostTotal as the expression.
Answer: D
Explanation:
Note: A named calculation is a SQL expression represented as a calculated column. This expression appears and behaves as a column in the table. A named calculation lets you extend the relational schema of existing tables or views in a data source view without modifying the tables or views in the underlying data source. For example, a common calculated value derived from the columns of a fact table can be expressed as a single named calculation in the data source view, instead of modifying the underlying database table or creating a view in the underlying database. A named calculation can also be used in place of calculated member in each cube based on the data source view. Named calculations are calculated during processing whereas calculated members are calculated at query time.
A named calculation is also frequently used to construct a user friendly name for a dimension member.
Reference: Define Named Calculations in a Data Source View (Analysis Services)
QUESTION 208
You maintain a SQL Server 2008 Analysis Services (SSAS) instance.
You are developing a new data mining structure.
You need to set the Microsoft Clustering Algorithm to meet the following requirements:
– Allow data points to be assigned to two clusters.
– Generate a probability for each combination of data point and cluster.
– Provide the fastest results on large datasets (greater than one million records).
Which clustering method should you use?
A. Scalable Expectation Maximization (EM)
B. Non-scalable Expectation Maximization (EM)
C. Non-scalable K-Means
D. Scalable K-Means
Answer: C
QUESTION 209
You create a SQL Server 2008 Analysis Services (SSAS) solution.
Your organization wants to track the times that products are ordered, shipped, and received in an existing cube.
You need to enable this tracking based on Sales, Orders, and Shipments fact tables.
What should you do?
A. Add many-to-many relationships between the Sales, Orders, and Shipments fact tables.
B. Add one Time dimension to each fact table.
C. Add a role-playing Time dimension to the cube via the Dimension Usage view.
D. Add a Time table to the underlying data and then add the table to the cube’s Data Source View.
Answer: C
QUESTION 210
You are a SQL Server 2008 Reporting Services (SSRS) developer.
You develop a report with two parameters named Region and City in that order.
When the Region parameter is selected, the City parameter should be filtered by the Region selected.
You need to enable this functionality.
What should you do?
A. Create a distinct dataset that includes all possible values and attach it to the parameter.
B. Create a dynamic dataset that utilizes the WHERE clause to filter by the parameter.
C. Create a dynamic data source from a dataset by using the IN operator.
D. Configure the Internal Visibility option for the parameter.
E. Change the dataset from a shared dataset to an embedded dataset in the report.
F. Create a dynamic data source from a dataset that includes a list of distinct servers.
G. Create a dynamic dataset that includes a list of the different users.
H. Configure the Hidden Visibility property.
Answer: B
QUESTION 211
You create a SQL Server 2008 Reporting Services (SSRS) report.
The report is hosted in a SharePoint environment.
The UserID is passed into the report automatically when the user views the report.
The UserID will be used to link to other pages on the SharePoint site via url.
You need to prevent the user from seeing their UserID.
What should you do?
A. Create a distinct dataset that includes all possible values and attach it to the parameter.
B. Create a dynamic dataset that utilizes the WHERE clause to filter by the parameter.
C. Create a dynamic data source from a dataset by using the IN operator.
D. Configure the Internal Visibility option for the parameter.
E. Change the dataset from a shared dataset to an embedded dataset in the report.
F. Create a dynamic data source from a dataset that includes a list of distinct servers.
G. Create a dynamic dataset that includes a list of the different users.
H. Configure the Hidden Visibility property.
Answer: H
QUESTION 212
You develop a SQL Server 2008 Reporting Services (SSRS) instance of a report model.
The organization requires that users of a report be able to dynamically change the server environment.
You need to create a parameter that gives the user the option to choose the server before report execution.
What should you do?
A. Create a distinct dataset that includes all possible values and attach it to the parameter.
B. Create a dynamic dataset that utilizes the WHERE clause to filter by the parameter.
C. Create a dynamic data source from a dataset by using the IN operator.
D. Configure the Internal Visibility option for the parameter.
E. Change the dataset from a shared dataset to an embedded dataset in the report.
F. Create a dynamic data source from a dataset that includes a list of distinct servers.
G. Create a dynamic dataset that includes a list of the different users.
H. Configure the Hidden Visibility property.
Answer: F
QUESTION 213
Drag and Drop Question
You have a SQL Server 2008 Reporting Services (SSRS) Enterprise Edition instance.
You need to add a second report server to this instance.
In which order should you perform the steps?
(To answer, move the appropriate five actions from the list of actions to the answer area and arrange them in the correct order.)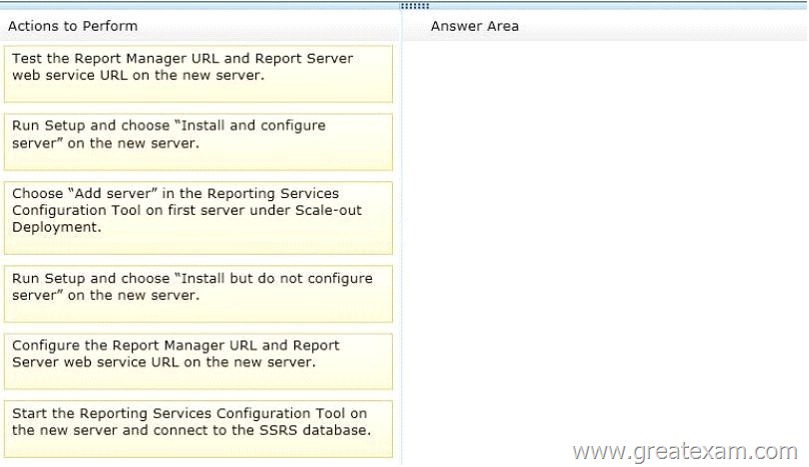
Answer: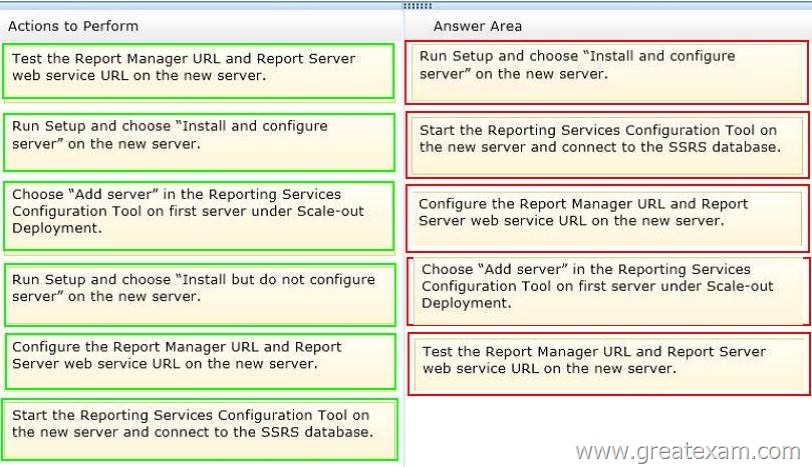
QUESTION 214
You maintain a SQL Server 2008 Reporting Services (SSRS) instance for a shoe company.
An existing report on shoe sales allows the user to see the company’s revenue across many different attributes.
You need to create a drop down list that filters the report by one or more shoe colors.
You alter the main dataset and configure the report parameter to accept multiple values.
What should you do next?
A. Create a distinct dataset that includes all possible values and attach it to the parameter.
B. Create a dynamic dataset that utilizes the WHERE clause to filter by the parameter.
C. Create a dynamic data source from a dataset by using the IN operator.
D. Configure the Internal Visibility option for the parameter.
E. Change the dataset from a shared dataset to an embedded dataset in the report.
F. Create a dynamic data source from a dataset that includes a list of distinct servers.
G. Create a dynamic dataset that includes a list of the different users.
H. Configure the Hidden Visibility property.
Answer: A
QUESTION 215
You develop reports by using SQL Server 2008 Reporting Services (SSRS) Enterprise Edition.
You need to use data-driven subscription to distribute reports based on dynamic subscription data.
Which role should you use?
A. Publisher
B. System User
C. Content Manager
D. Browser
Answer: C
QUESTION 216
You are responsible for the SQL Server 2008 Integration Services (SSIS) instance at your organization. This instance uses SQL Server Authentication.
Other developers develop, configure, and deploy packages to the MSDB database.
You need to determine whether a package named “DailyLoad” exists in the MSDB database on the local instance of SQL Server.
What is the correct dtutil command syntax?
A. dtutil /FILE W:/DailyLoad.dtsx /EXISTS
B. dtutil /SQL DailyLoad /EXISTS
C. dtutil SQL DailyLoad /USERNAME xyz /OSERPASSWORD xxxxxx /EXISTS
D. dtutil /DTS DailyLoad.dtsx /MOVE SQL; destPackage
Answer: C
QUESTION 217
You maintain the SQL Server 2008 Integration Services (SSIS) instance for a healthcare device manufacturing company.
You develop a package named Memberinformation.dtsx with Windows authentication.
You deploy it to SQL Server.
You need to validate Memberinformation.dtsx packages without package execution.
Which command syntax should you use?
A. dtexec /sq Memberinformation /verifyv {a400e860-38d5-11c5-11ce-ae62-08002b2b79ef}
B. dtexec /sq Memberinformation /ser productionServer /va
C. dtexec /f “Z:\Memberinxormation.dtsx” /conf “Z:\Memberiniormationconfig.cfg”
D. dtexec /f “2:\Member^nformation.dtsx” /l “DTS.LogProviderTextFile;2:\loginformation.txt”
Answer: C
QUESTION 218
You are a BI developer for a financial firm.
You are developing a SQL Server 2008 Integration Services (SSIS) instance to load 13 million records into TABLE_C three times daily from TABLE_A and TABLE_B.
TABLE_A is in DATABASE_A hosted on SERVER_A. TABLE_B is in DATABASE_B hosted on SERVER_B. TABLE_C is in DATABASE_C hosted on SERVER_C.
You are logged on to SERVER_C.
You have read-only permissions on SERVER_A and SERVER_B. These two servers are on different domains with individual firewall settings.
You need to load the records into TABLE_C by performing an inner join on TABLE_A and TABLE_B.
What should you do?
A. Configure SERVER_A and SERVER_B as linked servers.
B. Install the SSIS instance on both SERVER_A and SERVER_B.
C. Write store procedures to pull data from SERVER_A and SERVER_B.
D. Install the SSIS instance on SERVER_C and develop an SSIS package with the merge join component.
Answer: D
QUESTION 219
You develop a package in SQL Server 2008 Integration Services (SSIS).
You need to deploy the package so that it meets the following requirements:
– Only authorized users can view and execute the package.
– Users will NOT know the database credentials from within the package.
– The package should NOT be stored in the MSDB database.
What should you do?
A. Set the protection level to DontSaveSensitive.
B. Set the protection level to EncryptSensitiveWithPassword.
C. Set the protection level to ServerStorage.
D. Set the protection level to EncryptAIIWithUserKey.
Answer: D
Explanation:
EncryptAllWithUserKey
Encrypts the entire package by using keys based on the user profile.
Only the same user using the same profile can load the package.
Note:
* ProtectionLevel
The protection level of the package. The values are DontSaveSensitive, EncryptSensitiveWithUserKey, EncryptSensitiveWithPassword, EncryptAllWithPassword, and ServerStorage. The default value of this property is EncryptSensitiveWithUserKey.
Incorrect:
Not A: DontSaveSensitive
Sensitive information is not saved in the package. The sensitive information is removed and replaced with blanks.
Not C: ServerStorage
Encrypts the package within a SQL Server msdb database. This option is supported only when a package is saved to SQL Server. It is not supported when a package is saved to the File System. The access control of who can decrypt the package is controlled by SQL Server database roles.
Not D: EncryptSensitiveWithPassword
Encrypts only sensitive information contained in the package by using a password. DPAPI is used for this encryption.
Reference: DTSProtectionLevel Enumeration
QUESTION 220
You maintain the SQL Server 2008 Integration Services (SSIS) instance for a healthcare supply chain data management company.
Your company uses a third-party event based scheduler.
You develop a package named Memberinformation.dtsx and save it in the SSISpackages folder on the company network.
You need to deploy this package to the ProdSSISpackages file system on the production server. You need to rename the package to Memberinformation_Prod.dtsx, and the event based scheduler will execute the renamed package.
Which command syntax should you use?
A. dtutil /FILE c:\ SSISpackagesXMemberInformation.dtsx /DestServer DBPROD /COPY SQL;
MemberInformation_Prod.dtsx
B. dtutil /SQL Member-Information /COPY DTS;c:
\SSISpacckages\MemberInformation_Prod
C. dtutil /FILE c:\SSISpackages\MemberInformation.dtsx /COPY SQL; MemberInformation_Prod.dtsx
D. dtutil /FILE c:\SSISpackages\Memberinformation.dtsx /COPY FILE;
W:\ProdSSISpackagea \MemberInformation Prod.dtax
Answer: D
GreatExam offers the latest 70-448 PDF and VCE dumps with new version VCE player for free download, and the new 70-448 practice test ensures your exam 100% pass.
http://www.greatexam.com/70-448-exam-questions.html